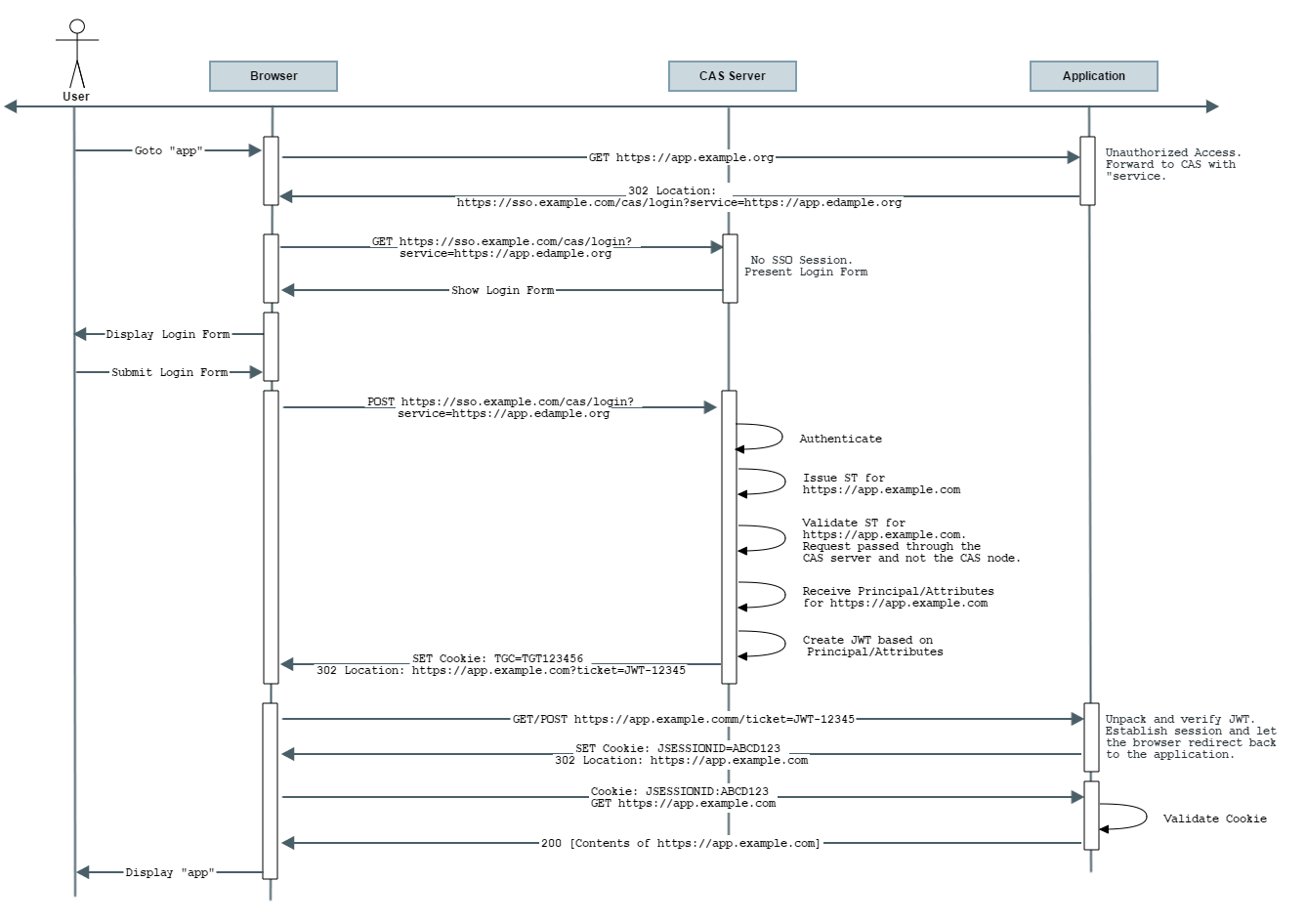
JWT Service Tickets
JSON Web Tokens are an open, industry standard RFC 7519 method for representing claims securely between two parties. CAS may also be allowed to fully create signed/encrypted JWTs and pass them back to the application in form of service tickets.
JWTs are entirely self-contained and contain the authenticated principal as well as all authorized attributes in form of JWT claims.
Make sure you have the proper JCE bundle installed in your Java
environment that is used by CAS, specially if you need to use specific signing/encryption algorithms and methods. Be sure to pick
the right version of the JCE for your Java version. Java versions can be detected via the java -version command.
Overview
JWT-based service tickets are issued to application based on the same semantics defined by the CAS Protocol.
CAS having received an authentication request via its /login endpoint will conditionally issue back JWT service tickets to the
application in form of a ticket parameter via the requested http method.
All JWTs are by default signed and encrypted by CAS based on keys generated and controlled during deployment. Such keys may be exchanged with client applications to unpack the JWT and access claims.
Flow Diagram
Note that per the above diagram, the JWT request by default internally causes CAS to generate an ST for the application and immediately then validate it in
order to get access to the authenticated principal and attributes per policies associated with the application registration record in the
CAS service registry. This response is transformed into a JWT that is then passed onto the client application.
In other words, the responsibility of receiving a service ticket (ST) and validating it is all moved into and handled internally by CAS.
The application only needs to learn how to decipher and unpack the final JWT and ensure its validity.
The expiration time of the generated JWT is controlled by the length of the assertion returned as part of the validation event. If the
assertion validity length is not specified, then the expiration time is controlled by the length of the SSO session defined as part of SSO expiration policy of the CAS server.
Remember that you are just receiving a ticket in form of a JWT, thereby removing the need from your client to validate a normal service ticket. The ticket is internally validated by CAS and you as the client are only left in charge of validating the JWT itself. Do not confuse this with OpenID Connect. While a JWT, the token itself is not an ID token, cannot be refreshed and must be obtained again once you deem it expired. If you need more, consider using the OpenID Connect protocol instead. Note that the responsibility of validating the JWT is pushed onto the client and NOT the CAS server itself.
Actuator Endpoints
The following endpoints are provided by CAS:
The following settings and properties are available from the CAS configuration catalog:
- Required
- Optional
- Signing & Encryption
- Hibernate & JDBC
- Email Servers
- LDAP & Active Directory
- Authentication
- Password Encoding
- Principal Transformation
- Password Policy
cas.monitor.endpoints.jdbc.password-encoder.encoding-algorithm=
The encoding algorithm to use such as
CAS Property:
|
1 | cas.monitor.endpoints.jdbc.password-encoder.encoding-algorithm=... |
1
cas:
monitor:
endpoints:
jdbc:
password-encoder:
encoding-algorithm: "..."
1
java -Dcas.monitor.endpoints.jdbc.password-encoder.encoding-algorithm="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PASSWORD_ENCODER_ENCODING_ALGORITHM="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.password-encoder.encoding-algorithm="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.password-encoder.type=NONE
Define the password encoder type to use. Type may be specified as blank or NONE to disable password encoding. It may also refer to a fully-qualified class name that implements the Spring Security's PasswordEncoder interface if you wish you define your own encoder.
NONE: No password encoding (i.e. plain-text) takes place.DEFAULT: Use theDefaultPasswordEncoderof CAS. For message-digest algorithms viacharacter-encodingandencoding-algorithm.BCRYPT: Use theBCryptPasswordEncoderbased on the strength provided and an optional secret.SCRYPT: Use theSCryptPasswordEncoder.PBKDF2: Use thePbkdf2PasswordEncoderbased on the strength provided and an optional secret.STANDARD: Use theStandardPasswordEncoderbased on the secret provided.SSHA: Use theLdapShaPasswordEncodersupports Ldap SHA and SSHA (salted-SHA). The values are base-64 encoded and have the label {SHA} or {SSHA} prepended to the encoded hash.GLIBC_CRYPT: Use theGlibcCryptPasswordEncoderbased on theencoding-algorithm, strength provided and an optional secret.org.example.MyEncoder: An implementation ofPasswordEncoderof your own choosing.file:///path/to/script.groovy: Path to a Groovy script charged with handling password encoding operations.
org.apereo.cas.configuration.model.core.authentication.PasswordEncoderProperties.
CAS Property: cas.monitor.endpoints.jdbc.password-encoder.type
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.password-encoder.type=NONE
1
cas:
monitor:
endpoints:
jdbc:
password-encoder:
type: "NONE"
1
java -Dcas.monitor.endpoints.jdbc.password-encoder.type="NONE" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PASSWORD_ENCODER_TYPE="NONE"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.password-encoder.type="NONE"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.driver-class=org.hsqldb.jdbcDriver
The JDBC driver used to connect to the database.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.driver-class
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.driver-class=org.hsqldb.jdbcDriver
1
cas:
monitor:
endpoints:
jdbc:
driver-class: "org.hsqldb.jdbcDriver"
1
java -Dcas.monitor.endpoints.jdbc.driver-class="org.hsqldb.jdbcDriver" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_DRIVER_CLASS="org.hsqldb.jdbcDriver"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.driver-class="org.hsqldb.jdbcDriver"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.password=
The database connection password.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.password
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.password=...
1
cas:
monitor:
endpoints:
jdbc:
password: "..."
1
java -Dcas.monitor.endpoints.jdbc.password="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PASSWORD="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.password="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.url=jdbc:hsqldb:mem:cas-hsql-database
The database connection URL.
This setting supports the Spring Expression Language.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.url
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.url=jdbc:hsqldb:mem:cas-hsql-database
1
cas:
monitor:
endpoints:
jdbc:
url: "jdbc:hsqldb:mem:cas-hsql-database"
1
java -Dcas.monitor.endpoints.jdbc.url="jdbc:hsqldb:mem:cas-hsql-database" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_URL="jdbc:hsqldb:mem:cas-hsql-database"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.url="jdbc:hsqldb:mem:cas-hsql-database"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.user=sa
The database user.
The database user must have sufficient permissions to be able to handle schema changes and updates, when needed. org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.user
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.user=sa
1
cas:
monitor:
endpoints:
jdbc:
user: "sa"
1
java -Dcas.monitor.endpoints.jdbc.user="sa" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_USER="sa"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.user="sa"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.password-encoder.character-encoding=UTF-8
The encoding algorithm to use such as 'UTF-8'. Relevant when the type used is
CAS Property:
|
1 | cas.monitor.endpoints.jdbc.password-encoder.character-encoding=UTF-8 |
1
cas:
monitor:
endpoints:
jdbc:
password-encoder:
character-encoding: "UTF-8"
1
java -Dcas.monitor.endpoints.jdbc.password-encoder.character-encoding="UTF-8" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PASSWORD_ENCODER_CHARACTER_ENCODING="UTF-8"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.password-encoder.character-encoding="UTF-8"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.password-encoder.hash-length=16
When used by PasswordEncoderTypes#ARGON2, it indicates the hash strength/length.
org.apereo.cas.configuration.model.core.authentication.PasswordEncoderProperties.
CAS Property: cas.monitor.endpoints.jdbc.password-encoder.hash-length
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.password-encoder.hash-length=16
1
cas:
monitor:
endpoints:
jdbc:
password-encoder:
hash-length: "16"
1
java -Dcas.monitor.endpoints.jdbc.password-encoder.hash-length="16" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PASSWORD_ENCODER_HASH_LENGTH="16"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.password-encoder.hash-length="16"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.password-encoder.secret=
Secret to use with PasswordEncoderTypes#STANDARD, PasswordEncoderTypes#PBKDF2, PasswordEncoderTypes#BCRYPT, PasswordEncoderTypes#GLIBC_CRYPT password encoders. Secret usually is an optional setting.
org.apereo.cas.configuration.model.core.authentication.PasswordEncoderProperties.
CAS Property: cas.monitor.endpoints.jdbc.password-encoder.secret
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.password-encoder.secret=...
1
cas:
monitor:
endpoints:
jdbc:
password-encoder:
secret: "..."
1
java -Dcas.monitor.endpoints.jdbc.password-encoder.secret="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PASSWORD_ENCODER_SECRET="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.password-encoder.secret="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.password-encoder.strength=16
Strength or number of iterations to use for password hashing. Usually relevant when dealing with PasswordEncoderTypes#PBKDF2, PasswordEncoderTypes#BCRYPT or PasswordEncoderTypes#GLIBC_CRYPT. When used by PasswordEncoderTypes#ARGON2, it indicates the salt strength.
org.apereo.cas.configuration.model.core.authentication.PasswordEncoderProperties.
CAS Property: cas.monitor.endpoints.jdbc.password-encoder.strength
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.password-encoder.strength=16
1
cas:
monitor:
endpoints:
jdbc:
password-encoder:
strength: "16"
1
java -Dcas.monitor.endpoints.jdbc.password-encoder.strength="16" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PASSWORD_ENCODER_STRENGTH="16"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.password-encoder.strength="16"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.autocommit=false
The default auto-commit behavior of connections in the pool. Determined whether queries such as update/insert should be immediately executed without waiting for an underlying transaction.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.autocommit
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.autocommit=...
1
cas:
monitor:
endpoints:
jdbc:
autocommit: "..."
1
java -Dcas.monitor.endpoints.jdbc.autocommit="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_AUTOCOMMIT="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.autocommit="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.batch-size=100
A non-zero value enables use of JDBC2 batch updates by Hibernate. e.g. recommended values between 5 and 30.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.batch-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.batch-size=100
1
cas:
monitor:
endpoints:
jdbc:
batch-size: "100"
1
java -Dcas.monitor.endpoints.jdbc.batch-size="100" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_BATCH_SIZE="100"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.batch-size="100"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.data-source-name=
Attempts to do a JNDI data source look up for the data source name specified. Will attempt to locate the data source object as is.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.data-source-name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.data-source-name=...
1
cas:
monitor:
endpoints:
jdbc:
data-source-name: "..."
1
java -Dcas.monitor.endpoints.jdbc.data-source-name="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_DATA_SOURCE_NAME="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.data-source-name="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.ddl-auto=update
Hibernate feature to automatically validate and exports DDL to the schema. By default, creates and drops the schema automatically when a session is starts and ends. Setting the value to validate or none may be more desirable for production, but any of the following options can be used:
validate: Validate the schema, but make no changes to the database.update: Update the schema.create: Create the schema, destroying previous data.create-drop: Drop the schema at the end of the session.none: Do nothing.
create-drop will result in the loss of all data as soon as CAS is started. For transient data like tickets this is probably not an issue, but in cases like the audit table important data could be lost. Using `update`, while safe for data, is confirmed to result in invalid database state. validate or none settings are likely the only safe options for production use. For more info, see this.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.ddl-auto
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.ddl-auto=update
1
cas:
monitor:
endpoints:
jdbc:
ddl-auto: "update"
1
java -Dcas.monitor.endpoints.jdbc.ddl-auto="update" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_DDL_AUTO="update"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.ddl-auto="update"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.default-catalog=
Qualifies unqualified table names with the given catalog in generated SQL.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.default-catalog
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.default-catalog=...
1
cas:
monitor:
endpoints:
jdbc:
default-catalog: "..."
1
java -Dcas.monitor.endpoints.jdbc.default-catalog="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_DEFAULT_CATALOG="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.default-catalog="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.default-schema=
Qualify unqualified table names with the given schema/tablespace in generated SQL.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.default-schema
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.default-schema=...
1
cas:
monitor:
endpoints:
jdbc:
default-schema: "..."
1
java -Dcas.monitor.endpoints.jdbc.default-schema="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_DEFAULT_SCHEMA="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.default-schema="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.dialect=org.hibernate.dialect.HSQLDialect
The database dialect is a configuration setting for platform independent software (JPA, Hibernate, etc) which allows such software to translate its generic SQL statements into vendor specific DDL, DML.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.dialect
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.dialect=org.hibernate.dialect.HSQLDialect
1
cas:
monitor:
endpoints:
jdbc:
dialect: "org.hibernate.dialect.HSQLDialect"
1
java -Dcas.monitor.endpoints.jdbc.dialect="org.hibernate.dialect.HSQLDialect" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_DIALECT="org.hibernate.dialect.HSQLDialect"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.dialect="org.hibernate.dialect.HSQLDialect"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.fail-fast-timeout=1
Set the pool initialization failure timeout.
- Any value greater than zero will be treated as a timeout for pool initialization. The calling thread will be blocked from continuing until a successful connection to the database, or until the timeout is reached. If the timeout is reached, then a
PoolInitializationExceptionwill be thrown. - A value of zero will not prevent the pool from starting in the case that a connection cannot be obtained. However, upon start the pool will attempt to obtain a connection and validate that the
connectionTestQueryandconnectionInitSqlare valid. If those validations fail, an exception will be thrown. If a connection cannot be obtained, the validation is skipped and the the pool will start and continue to try to obtain connections in the background. This can mean that callers toDataSource#getConnection()may encounter exceptions. - A value less than zero will not bypass any connection attempt and validation during startup, and therefore the pool will start immediately. The pool will continue to try to obtain connections in the background. This can mean that callers to
DataSource#getConnection()may encounter exceptions.
connectionTimeout or validationTimeout; they will be honored before this timeout is applied. The default value is one millisecond.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.fail-fast-timeout
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.fail-fast-timeout=1
1
cas:
monitor:
endpoints:
jdbc:
fail-fast-timeout: "1"
1
java -Dcas.monitor.endpoints.jdbc.fail-fast-timeout="1" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_FAIL_FAST_TIMEOUT="1"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.fail-fast-timeout="1"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.fetch-size=100
Used to specify number of rows to be fetched in a select query.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.fetch-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.fetch-size=100
1
cas:
monitor:
endpoints:
jdbc:
fetch-size: "100"
1
java -Dcas.monitor.endpoints.jdbc.fetch-size="100" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_FETCH_SIZE="100"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.fetch-size="100"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.generate-statistics=false
Allow hibernate to generate query statistics.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.generate-statistics
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.generate-statistics=...
1
cas:
monitor:
endpoints:
jdbc:
generate-statistics: "..."
1
java -Dcas.monitor.endpoints.jdbc.generate-statistics="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_GENERATE_STATISTICS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.generate-statistics="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.health-query=
The SQL query to be executed to test the validity of connections. This is for "legacy" databases that do not support the JDBC4 Connection.isValid() API.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.health-query
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.health-query=...
1
cas:
monitor:
endpoints:
jdbc:
health-query: "..."
1
java -Dcas.monitor.endpoints.jdbc.health-query="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_HEALTH_QUERY="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.health-query="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.idle-timeout=PT10M
Controls the maximum amount of time that a connection is allowed to sit idle in the pool.
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.idle-timeout
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.idle-timeout=PT10M
1
cas:
monitor:
endpoints:
jdbc:
idle-timeout: "PT10M"
1
java -Dcas.monitor.endpoints.jdbc.idle-timeout="PT10M" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_IDLE_TIMEOUT="PT10M"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.idle-timeout="PT10M"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.isolate-internal-queries=false
This property determines whether data source isolates internal pool queries, such as the connection alive test, in their own transaction.
Since these are typically read-only queries, it is rarely necessary to encapsulate them in their own transaction. This property only applies if#autocommit is disabled.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.isolate-internal-queries
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.isolate-internal-queries=...
1
cas:
monitor:
endpoints:
jdbc:
isolate-internal-queries: "..."
1
java -Dcas.monitor.endpoints.jdbc.isolate-internal-queries="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_ISOLATE_INTERNAL_QUERIES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.isolate-internal-queries="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.isolation-level-name=ISOLATION_READ_COMMITTED
Defines the isolation level for transactions. @see org.springframework.transaction.TransactionDefinition
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.isolation-level-name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.isolation-level-name=ISOLATION_READ_COMMITTED
1
cas:
monitor:
endpoints:
jdbc:
isolation-level-name: "ISOLATION_READ_COMMITTED"
1
java -Dcas.monitor.endpoints.jdbc.isolation-level-name="ISOLATION_READ_COMMITTED" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_ISOLATION_LEVEL_NAME="ISOLATION_READ_COMMITTED"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.isolation-level-name="ISOLATION_READ_COMMITTED"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.leak-threshold=3000
Controls the amount of time that a connection can be out of the pool before a message is logged indicating a possible connection leak.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.leak-threshold
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.leak-threshold=3000
1
cas:
monitor:
endpoints:
jdbc:
leak-threshold: "3000"
1
java -Dcas.monitor.endpoints.jdbc.leak-threshold="3000" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_LEAK_THRESHOLD="3000"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.leak-threshold="3000"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.physical-naming-strategy-class-name=org.apereo.cas.hibernate.CasHibernatePhysicalNamingStrategy
Fully-qualified name of the class that can control the physical naming strategy of hibernate.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.physical-naming-strategy-class-name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.physical-naming-strategy-class-name=org.apereo.cas.hibernate.CasHibernatePhysicalNamingStrategy
1
cas:
monitor:
endpoints:
jdbc:
physical-naming-strategy-class-name: "org.apereo.cas.hibernate.CasHibernatePhysicalNamingStrategy"
1
java -Dcas.monitor.endpoints.jdbc.physical-naming-strategy-class-name="org.apereo.cas.hibernate.CasHibernatePhysicalNamingStrategy" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PHYSICAL_NAMING_STRATEGY_CLASS_NAME="org.apereo.cas.hibernate.CasHibernatePhysicalNamingStrategy"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.physical-naming-strategy-class-name="org.apereo.cas.hibernate.CasHibernatePhysicalNamingStrategy"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.propagation-behavior-name=PROPAGATION_REQUIRED
Defines the propagation behavior for transactions. @see org.springframework.transaction.TransactionDefinition
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.propagation-behavior-name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.propagation-behavior-name=PROPAGATION_REQUIRED
1
cas:
monitor:
endpoints:
jdbc:
propagation-behavior-name: "PROPAGATION_REQUIRED"
1
java -Dcas.monitor.endpoints.jdbc.propagation-behavior-name="PROPAGATION_REQUIRED" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PROPAGATION_BEHAVIOR_NAME="PROPAGATION_REQUIRED"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.propagation-behavior-name="PROPAGATION_REQUIRED"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.properties=
Additional settings provided by Hibernate (or the connection provider) in form of key-value pairs.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.properties
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.properties=...
1
cas:
monitor:
endpoints:
jdbc:
properties: "..."
1
java -Dcas.monitor.endpoints.jdbc.properties="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_PROPERTIES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.properties="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.query=
Query to execute in order to authenticate users via JDBC. Example: SELECT username,password,enabled FROM users WHERE username=?
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.query
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.query=...
1
cas:
monitor:
endpoints:
jdbc:
query: "..."
1
java -Dcas.monitor.endpoints.jdbc.query="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_QUERY="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.query="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.read-only=false
Configures the Connections to be added to the pool as read-only Connections.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.read-only
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.read-only=...
1
cas:
monitor:
endpoints:
jdbc:
read-only: "..."
1
java -Dcas.monitor.endpoints.jdbc.read-only="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_READ_ONLY="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.read-only="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.role-prefix=
Prefix to add to the role.
org.apereo.cas.configuration.model.core.monitor.JdbcSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jdbc.role-prefix
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.role-prefix=...
1
cas:
monitor:
endpoints:
jdbc:
role-prefix: "..."
1
java -Dcas.monitor.endpoints.jdbc.role-prefix="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_ROLE_PREFIX="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.role-prefix="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.pool.keep-alive-time=0
This property controls the keepalive interval for a connection in the pool. An in-use connection will never be tested by the keepalive thread, only when it is idle will it be tested. Default is zero, which disables this feature.
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.support.ConnectionPoolingProperties.
CAS Property: cas.monitor.endpoints.jdbc.pool.keep-alive-time
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.pool.keep-alive-time=0
1
cas:
monitor:
endpoints:
jdbc:
pool:
keep-alive-time: "0"
1
java -Dcas.monitor.endpoints.jdbc.pool.keep-alive-time="0" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_POOL_KEEP_ALIVE_TIME="0"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.pool.keep-alive-time="0"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.pool.max-size=18
Controls the maximum number of connections to keep in the pool, including both idle and in-use connections.
org.apereo.cas.configuration.model.support.ConnectionPoolingProperties.
CAS Property: cas.monitor.endpoints.jdbc.pool.max-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.pool.max-size=18
1
cas:
monitor:
endpoints:
jdbc:
pool:
max-size: "18"
1
java -Dcas.monitor.endpoints.jdbc.pool.max-size="18" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_POOL_MAX_SIZE="18"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.pool.max-size="18"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.pool.max-wait=PT2S
Sets the maximum time in seconds that this data source will wait while attempting to connect to a database.
A value of zero specifies that the timeout is the default system timeout if there is one; otherwise, it specifies that there is no timeout. This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.support.ConnectionPoolingProperties.
CAS Property: cas.monitor.endpoints.jdbc.pool.max-wait
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.pool.max-wait=PT2S
1
cas:
monitor:
endpoints:
jdbc:
pool:
max-wait: "PT2S"
1
java -Dcas.monitor.endpoints.jdbc.pool.max-wait="PT2S" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_POOL_MAX_WAIT="PT2S"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.pool.max-wait="PT2S"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.pool.maximum-lifetime=PT10M
This property controls the maximum lifetime of a connection in the pool. When a connection reaches this timeout, even if recently used, it will be retired from the pool. An in-use connection will never be retired, only when it is idle will it be removed.
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.support.ConnectionPoolingProperties.
CAS Property: cas.monitor.endpoints.jdbc.pool.maximum-lifetime
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.pool.maximum-lifetime=PT10M
1
cas:
monitor:
endpoints:
jdbc:
pool:
maximum-lifetime: "PT10M"
1
java -Dcas.monitor.endpoints.jdbc.pool.maximum-lifetime="PT10M" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_POOL_MAXIMUM_LIFETIME="PT10M"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.pool.maximum-lifetime="PT10M"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.pool.min-size=6
Controls the minimum size that the pool is allowed to reach, including both idle and in-use connections.
org.apereo.cas.configuration.model.support.ConnectionPoolingProperties.
CAS Property: cas.monitor.endpoints.jdbc.pool.min-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.pool.min-size=6
1
cas:
monitor:
endpoints:
jdbc:
pool:
min-size: "6"
1
java -Dcas.monitor.endpoints.jdbc.pool.min-size="6" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_POOL_MIN_SIZE="6"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.pool.min-size="6"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.pool.name=
Set the name of the connection pool. This is primarily used for the MBean to uniquely identify the pool configuration.
org.apereo.cas.configuration.model.support.ConnectionPoolingProperties.
CAS Property: cas.monitor.endpoints.jdbc.pool.name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.pool.name=...
1
cas:
monitor:
endpoints:
jdbc:
pool:
name: "..."
1
java -Dcas.monitor.endpoints.jdbc.pool.name="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_POOL_NAME="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.pool.name="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.pool.suspension=false
Whether or not pool suspension is allowed.
There is a performance impact when pool suspension is enabled. Unless you need it (for a redundancy system for example) do not enable it. org.apereo.cas.configuration.model.support.ConnectionPoolingProperties.
CAS Property: cas.monitor.endpoints.jdbc.pool.suspension
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.pool.suspension=...
1
cas:
monitor:
endpoints:
jdbc:
pool:
suspension: "..."
1
java -Dcas.monitor.endpoints.jdbc.pool.suspension="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_POOL_SUSPENSION="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.pool.suspension="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jdbc.pool.timeout-millis=1000
The maximum number of milliseconds that the pool will wait for a connection to be validated as alive.
org.apereo.cas.configuration.model.support.ConnectionPoolingProperties.
CAS Property: cas.monitor.endpoints.jdbc.pool.timeout-millis
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jdbc.pool.timeout-millis=1000
1
cas:
monitor:
endpoints:
jdbc:
pool:
timeout-millis: "1000"
1
java -Dcas.monitor.endpoints.jdbc.pool.timeout-millis="1000" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JDBC_POOL_TIMEOUT_MILLIS="1000"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jdbc.pool.timeout-millis="1000"
cas.war
with an embedded server container and can be found in the build/libs directory.
Control global properties that are relevant to Hibernate, when CAS attempts to employ and utilize database resources, connections and queries.
cas.jdbc.case-insensitive=false
When choosing physical table names, determine whether names should be considered case-insensitive. How can I configure this property?
CAS Property:
|
1 | cas.jdbc.case-insensitive=... |
1
cas:
jdbc:
case-insensitive: "..."
1
java -Dcas.jdbc.case-insensitive="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_JDBC_CASE_INSENSITIVE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.jdbc.case-insensitive="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.jdbc.gen-ddl=true
Whether to generate DDL after the EntityManagerFactory has been initialized creating/updating all relevant tables.
How can I configure this property?
CAS Property: cas.jdbc.gen-ddl
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.jdbc.gen-ddl=true
1
cas:
jdbc:
gen-ddl: "true"
1
java -Dcas.jdbc.gen-ddl="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_JDBC_GEN_DDL="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.jdbc.gen-ddl="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.jdbc.physical-table-names=
Indicate a physical table name to be used by the hibernate naming strategy in case table names need to be customized for the specific type of database. The key here indicates the CAS-provided table name and the value is the translate physical name for the database. If a match is not found for the CAS-provided table name, then that name will be used by default.
How can I configure this property?
CAS Property: cas.jdbc.physical-table-names
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.jdbc.physical-table-names=...
1
cas:
jdbc:
physical-table-names: "..."
1
java -Dcas.jdbc.physical-table-names="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_JDBC_PHYSICAL_TABLE_NAMES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.jdbc.physical-table-names="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.jdbc.show-sql=false
Whether SQL queries should be displayed in the console/logs.
How can I configure this property?
CAS Property: cas.jdbc.show-sql
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.jdbc.show-sql=...
1
cas:
jdbc:
show-sql: "..."
1
java -Dcas.jdbc.show-sql="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_JDBC_SHOW_SQL="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.jdbc.show-sql="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
If you need to design your own password encoding scheme where the type is specified as a fully qualified Java class name, the structure of the class would be similar to the following:
1
2
3
4
5
6
7
8
9
10
11
package org.example.cas;
import org.springframework.security.crypto.codec.*;
import org.springframework.security.crypto.password.*;
public class MyEncoder extends AbstractPasswordEncoder {
@Override
protected byte[] encode(CharSequence rawPassword, byte[] salt) {
return ...
}
}
If you need to design your own password encoding scheme where the type is specified as a path to a Groovy script, the structure of the script would be similar to the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
import java.util.*
byte[] run(final Object... args) {
def rawPassword = args[0]
def generatedSalt = args[1]
def logger = args[2]
def casApplicationContext = args[3]
logger.debug("Encoding password...")
return ...
}
Boolean matches(final Object... args) {
def rawPassword = args[0]
def encodedPassword = args[1]
def logger = args[2]
def casApplicationContext = args[3]
logger.debug("Does match or not ?");
return ...
The following settings and properties are available from the CAS configuration catalog:
- Required
- Optional
- Signing & Encryption
- Hibernate & JDBC
- Email Servers
- LDAP & Active Directory
- Authentication
- Password Encoding
- Principal Transformation
- Password Policy
cas.monitor.endpoints.ldap.base-dn=
Base DN to use. There may be scenarios where different parts of a single LDAP tree could be considered as base-dns. Rather than duplicating the LDAP configuration block for each individual base-dn, each entry can be specified and joined together using a special delimiter character. The user DN is retrieved using the combination of all base-dn and DN resolvers in the order defined. DN resolution should fail if multiple DNs are found. Otherwise the first DN found is returned. Usual syntax is:
CAS Property:
|
1 | cas.monitor.endpoints.ldap.base-dn=... |
1
cas:
monitor:
endpoints:
ldap:
base-dn: "..."
1
java -Dcas.monitor.endpoints.ldap.base-dn="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_BASE_DN="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.base-dn="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.bind-credential=
The bind credential to use when connecting to LDAP.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.bind-credential
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.bind-credential=...
1
cas:
monitor:
endpoints:
ldap:
bind-credential: "..."
1
java -Dcas.monitor.endpoints.ldap.bind-credential="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_BIND_CREDENTIAL="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.bind-credential="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.bind-dn=
The bind DN to use when connecting to LDAP. LDAP connection configuration injected into the LDAP connection pool can be initialized with the following parameters:
bindDn/bindCredentialprovided - Use the provided credentials to bind when initializing connections.bindDn/bindCredentialset to*- Use a fast-bind strategy to initialize the pool.bindDn/bindCredentialset to blank - Skip connection initializing; perform operations anonymously.- SASL mechanism provided - Use the given SASL mechanism to bind when initializing connections.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.bind-dn
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.bind-dn=...
1
cas:
monitor:
endpoints:
ldap:
bind-dn: "..."
1
java -Dcas.monitor.endpoints.ldap.bind-dn="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_BIND_DN="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.bind-dn="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-url=
The LDAP url to the server. More than one may be specified, separated by space and/or comma.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-url
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-url=...
1
cas:
monitor:
endpoints:
ldap:
ldap-url: "..."
1
java -Dcas.monitor.endpoints.ldap.ldap-url="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_URL="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-url="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-filter=
User filter to use for searching. Syntax is cn={user} or cn={0}.
file:/path/to/GroovyScript.groovy to fully build the final filter template dynamically.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.search-filter
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-filter=...
1
cas:
monitor:
endpoints:
ldap:
search-filter: "..."
1
java -Dcas.monitor.endpoints.ldap.search-filter="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_FILTER="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-filter="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.type=AUTHENTICATED
The authentication type.
AD- Users authenticate withsAMAccountName.AUTHENTICATED- Manager bind/search type of authentication. If {} principalAttributePassword} is empty then a user simple bind is done to validate credentials. Otherwise the given attribute is compared with the givenprincipalAttributePasswordusing theSHAencrypted value of it.</li>ANONYMOUS: Similar semantics asAUTHENTICATEDexcept nobindDnandbindCredentialmay be specified to initialize the connection. IfprincipalAttributePasswordis empty then a user simple bind is done to validate credentials. Otherwise the given attribute is compared with the givenprincipalAttributePasswordusing theSHAencrypted value of it.- DIRECT: Direct Bind - Compute user DN from format string and perform simple bind. This is relevant when no search is required to compute the DN needed for a bind operation. Use cases for this type are: 1) All users are under a single branch in the directory,
</ul> Available values are as follows:e.g. ou=Users,dc=example,dc=org.2) The username provided on the CAS login form is part of the DN, e.g.uid=%s,ou=Users,dc=example,dc=org.AD: Active Directory.AUTHENTICATED: Authenticated Search.DIRECT: Direct Bind.ANONYMOUS: Anonymous Search.
How can I configure this property?org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.</div></td> </tr>CAS Property:
cas.monitor.endpoints.ldap.typeConfiguration properties can be included and activated using the following strategies.:information_source: NoteWhen possible, properties should be stored in lower-case kebab format, such as
cas.property-name=value. The only possible exception to this rule is when naming actuator endpoints; The name of the actuator endpoints (i.e.ssoSessions) MUST remain in camelCase mode.CAS properties can be specified using the Java configuration property syntax in any and all.propertiesfiles:This is the most common form of property configuration that is recognized by CAS, regardless of the actual property source, which might in fact be managed separately outside the CAS environment, by another system or cloud framework.1
cas.monitor.endpoints.ldap.type=AUTHENTICATED
CAS properties can be specified using the YAML syntax:Note that YAML is very specific about structure and indentation. Be sure to verify the correctness of the final result with your YAML validator of choice.1
cas:
monitor:
endpoints:
ldap:
type: "AUTHENTICATED"CAS properties can be passed to the CAS web application as system properties, when the application is launched:The above example assumes that the CAS web application is packaged as1
java -Dcas.monitor.endpoints.ldap.type="AUTHENTICATED" -jar build/libs/cas.war
cas.warwith an embedded server container and can be found in thebuild/libsdirectory. Note the placement of the system property which must be specified before the CAS web application is launched.CAS properties can specified as system environment variables before the CAS web application is launched:The above example assumes that the CAS web application is packaged as1 2 3
export CAS_MONITOR_ENDPOINTS_LDAP_TYPE="AUTHENTICATED" java -jar build/libs/cas.war
cas.warwith an embedded server container and can be found in thebuild/libsdirectory.CAS properties can be passed to the CAS web application as command-line arguments, when the application is launched:The above example assumes that the CAS web application is packaged as1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.type="AUTHENTICATED"
cas.warwith an embedded server container and can be found in thebuild/libsdirectory.
cas.monitor.endpoints.ldap.allow-multiple-dns=false
Whether search/query results are allowed to match on multiple DNs, or whether a single unique DN is expected for the result.
CAS Property:
|
1 | cas.monitor.endpoints.ldap.allow-multiple-dns=... |
1
cas:
monitor:
endpoints:
ldap:
allow-multiple-dns: "..."
1
java -Dcas.monitor.endpoints.ldap.allow-multiple-dns="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_ALLOW_MULTIPLE_DNS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.allow-multiple-dns="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.allow-multiple-entries=false
Set if multiple Entries are allowed.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.allow-multiple-entries
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.allow-multiple-entries=...
1
cas:
monitor:
endpoints:
ldap:
allow-multiple-entries: "..."
1
java -Dcas.monitor.endpoints.ldap.allow-multiple-entries="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_ALLOW_MULTIPLE_ENTRIES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.allow-multiple-entries="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.binary-attributes=
Indicate the collection of attributes that are to be tagged and processed as binary attributes by the underlying search resolver.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.binary-attributes
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.binary-attributes=...
1
cas:
monitor:
endpoints:
ldap:
binary-attributes: "..."
1
java -Dcas.monitor.endpoints.ldap.binary-attributes="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_BINARY_ATTRIBUTES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.binary-attributes="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.block-wait-time=PT3S
The length of time the pool will block. By default the pool will block indefinitely and there is no guarantee that waiting threads will be serviced in the order in which they made their request. This option should be used with a blocking connection pool when you need to control the exact number of connections that can be created
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.block-wait-time
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.block-wait-time=PT3S
1
cas:
monitor:
endpoints:
ldap:
block-wait-time: "PT3S"
1
java -Dcas.monitor.endpoints.ldap.block-wait-time="PT3S" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_BLOCK_WAIT_TIME="PT3S"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.block-wait-time="PT3S"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.connect-timeout=PT5S
Sets the maximum amount of time that connects will block.
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.connect-timeout
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.connect-timeout=PT5S
1
cas:
monitor:
endpoints:
ldap:
connect-timeout: "PT5S"
1
java -Dcas.monitor.endpoints.ldap.connect-timeout="PT5S" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_CONNECT_TIMEOUT="PT5S"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.connect-timeout="PT5S"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.connection-strategy=
If multiple URLs are provided as the ldapURL this describes how each URL will be processed.
ACTIVE_PASSIVEFirst LDAP will be used for every request unless it fails and then the next shall be used.ROUND_ROBINFor each new connection the next url in the list will be used.RANDOMFor each new connection a random LDAP url will be selected.DNS_SRVLDAP urls based on DNS SRV records of the configured/given LDAP url will be used.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.connection-strategy
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.connection-strategy=...
1
cas:
monitor:
endpoints:
ldap:
connection-strategy: "..."
1
java -Dcas.monitor.endpoints.ldap.connection-strategy="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_CONNECTION_STRATEGY="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.connection-strategy="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.deref-aliases=
Define how aliases are de-referenced. Accepted values are:
NEVERSEARCHING: dereference when searching the entries beneath the starting point but not when searching for the starting entry.FINDING: dereference when searching for the starting entry but not when searching the entries beneath the starting point.ALWAYS: dereference when searching for the starting entry and when searching the entries beneath the starting point.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.deref-aliases
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.deref-aliases=...
1
cas:
monitor:
endpoints:
ldap:
deref-aliases: "..."
1
java -Dcas.monitor.endpoints.ldap.deref-aliases="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_DEREF_ALIASES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.deref-aliases="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.disable-pooling=false
Whether to use a pooled connection factory in components.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.disable-pooling
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.disable-pooling=...
1
cas:
monitor:
endpoints:
ldap:
disable-pooling: "..."
1
java -Dcas.monitor.endpoints.ldap.disable-pooling="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_DISABLE_POOLING="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.disable-pooling="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.dn-format=
Specify the dn format accepted by the AD authenticator, etc. Example format might be uid=%s,ou=people,dc=example,dc=org.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.dn-format
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.dn-format=...
1
cas:
monitor:
endpoints:
ldap:
dn-format: "..."
1
java -Dcas.monitor.endpoints.ldap.dn-format="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_DN_FORMAT="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.dn-format="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.enhance-with-entry-resolver=true
Whether specific search entry resolvers need to be set on the authenticator, or the default should be used.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.enhance-with-entry-resolver
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.enhance-with-entry-resolver=true
1
cas:
monitor:
endpoints:
ldap:
enhance-with-entry-resolver: "true"
1
java -Dcas.monitor.endpoints.ldap.enhance-with-entry-resolver="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_ENHANCE_WITH_ENTRY_RESOLVER="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.enhance-with-entry-resolver="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.fail-fast=true
Attempt to populate the connection pool early on startup and fail quickly if something goes wrong.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.fail-fast
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.fail-fast=true
1
cas:
monitor:
endpoints:
ldap:
fail-fast: "true"
1
java -Dcas.monitor.endpoints.ldap.fail-fast="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_FAIL_FAST="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.fail-fast="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.follow-referrals=true
Set if search referrals should be followed.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.follow-referrals
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.follow-referrals=true
1
cas:
monitor:
endpoints:
ldap:
follow-referrals: "true"
1
java -Dcas.monitor.endpoints.ldap.follow-referrals="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_FOLLOW_REFERRALS="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.follow-referrals="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.hostname-verifier=DEFAULT
Hostname verification options. Available values are as follows:
DEFAULT: Default option, forcing verification.ANY: Skip hostname verification and allow all.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.hostname-verifier
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.hostname-verifier=DEFAULT
1
cas:
monitor:
endpoints:
ldap:
hostname-verifier: "DEFAULT"
1
java -Dcas.monitor.endpoints.ldap.hostname-verifier="DEFAULT" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_HOSTNAME_VERIFIER="DEFAULT"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.hostname-verifier="DEFAULT"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.idle-time=PT10M
Removes connections from the pool based on how long they have been idle in the available queue. Prunes connections that have been idle for more than the indicated amount.
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.idle-time
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.idle-time=PT10M
1
cas:
monitor:
endpoints:
ldap:
idle-time: "PT10M"
1
java -Dcas.monitor.endpoints.ldap.idle-time="PT10M" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_IDLE_TIME="PT10M"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.idle-time="PT10M"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.keystore=
Path to the keystore used for SSL connections. Typically contains SSL certificates for the LDAP server.
This setting supports the Spring Expression Language.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.keystore
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.keystore=...
1
cas:
monitor:
endpoints:
ldap:
keystore: "..."
1
java -Dcas.monitor.endpoints.ldap.keystore="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_KEYSTORE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.keystore="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.keystore-password=
Keystore password.
This setting supports the Spring Expression Language.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.keystore-password
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.keystore-password=...
1
cas:
monitor:
endpoints:
ldap:
keystore-password: "..."
1
java -Dcas.monitor.endpoints.ldap.keystore-password="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_KEYSTORE_PASSWORD="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.keystore-password="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.keystore-type=
The type of keystore. PKCS12 or JKS. If left blank, defaults to the default keystore type indicated by the underlying Java platform.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.keystore-type
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.keystore-type=...
1
cas:
monitor:
endpoints:
ldap:
keystore-type: "..."
1
java -Dcas.monitor.endpoints.ldap.keystore-type="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_KEYSTORE_TYPE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.keystore-type="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.max-pool-size=10
Maximum LDAP connection pool size which the pool can use to grow.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.max-pool-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.max-pool-size=10
1
cas:
monitor:
endpoints:
ldap:
max-pool-size: "10"
1
java -Dcas.monitor.endpoints.ldap.max-pool-size="10" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_MAX_POOL_SIZE="10"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.max-pool-size="10"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.min-pool-size=3
Minimum LDAP connection pool size. Size the pool should be initialized to and pruned to
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.min-pool-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.min-pool-size=3
1
cas:
monitor:
endpoints:
ldap:
min-pool-size: "3"
1
java -Dcas.monitor.endpoints.ldap.min-pool-size="3" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_MIN_POOL_SIZE="3"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.min-pool-size="3"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.name=
Name of the LDAP handler.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.name=...
1
cas:
monitor:
endpoints:
ldap:
name: "..."
1
java -Dcas.monitor.endpoints.ldap.name="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_NAME="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.name="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.page-size=0
Request that the server return results in batches of a specific size. See RFC 2696. This control is often used to work around server result size limits. A negative/zero value disables paged requests.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.page-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.page-size=0
1
cas:
monitor:
endpoints:
ldap:
page-size: "0"
1
java -Dcas.monitor.endpoints.ldap.page-size="0" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_PAGE_SIZE="0"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.page-size="0"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.pool-passivator=BIND
You may receive unexpected LDAP failures, when CAS is configured to authenticate using DIRECT or AUTHENTICATED types and LDAP is locked down to not allow anonymous binds/searches. Every second attempt with a given LDAP connection from the pool would fail if it was on the same connection as a failed login attempt, and the regular connection validator would similarly fail. When a connection is returned back to a pool, it still may contain the principal and credentials from the previous attempt. Before the next bind attempt using that connection, the validator tries to validate the connection again but fails because it’s no longer trying with the configured bind credentials but with whatever user DN was used in the previous step. Given the validation failure, the connection is closed and CAS would deny access by default. Passivators attempt to reconnect to LDAP with the configured bind credentials, effectively resetting the connection to what it should be after each bind request. Furthermore if you are seeing errors in the logs that resemble a 'Operation exception encountered, reopening connection' type of message, this usually is an indication that the connection pool’s validation timeout established and created by CAS is greater than the timeout configured in the LDAP server, or more likely, in the load balancer in front of the LDAP servers. You can adjust the LDAP server session’s timeout for connections, or you can teach CAS to use a validity period that is equal or less than the LDAP server session’s timeout. Accepted values are:
NONE: No passivation takes place.BIND: The default behavior which passivates a connection by performing a bind operation on it. This option requires the availability of bind credentials when establishing connections to LDAP.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.pool-passivator
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.pool-passivator=BIND
1
cas:
monitor:
endpoints:
ldap:
pool-passivator: "BIND"
1
java -Dcas.monitor.endpoints.ldap.pool-passivator="BIND" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_POOL_PASSIVATOR="BIND"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.pool-passivator="BIND"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.principal-attribute-password=
If principalAttributePassword is empty then a user simple bind is done to validate credentials otherwise the given attribute is compared with the given principalAttributePassword using the SHA encrypted value of it.
For the anonymous authentication type, if principalAttributePassword is empty then a user simple bind is done to validate credentials otherwise the given attribute is compared with the given principalAttributePassword using the SHA encrypted value of it. org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.principal-attribute-password
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.principal-attribute-password=...
1
cas:
monitor:
endpoints:
ldap:
principal-attribute-password: "..."
1
java -Dcas.monitor.endpoints.ldap.principal-attribute-password="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_PRINCIPAL_ATTRIBUTE_PASSWORD="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.principal-attribute-password="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.prune-period=PT2H
Removes connections from the pool based on how long they have been idle in the available queue. Run the pruning process at the indicated interval.
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.prune-period
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.prune-period=PT2H
1
cas:
monitor:
endpoints:
ldap:
prune-period: "PT2H"
1
java -Dcas.monitor.endpoints.ldap.prune-period="PT2H" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_PRUNE_PERIOD="PT2H"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.prune-period="PT2H"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.resolve-from-attribute=
If this attribute is set, the value found in the first attribute value will be used in place of the DN.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.resolve-from-attribute
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.resolve-from-attribute=...
1
cas:
monitor:
endpoints:
ldap:
resolve-from-attribute: "..."
1
java -Dcas.monitor.endpoints.ldap.resolve-from-attribute="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_RESOLVE_FROM_ATTRIBUTE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.resolve-from-attribute="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.response-timeout=PT5S
Duration of time to wait for responses.
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.response-timeout
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.response-timeout=PT5S
1
cas:
monitor:
endpoints:
ldap:
response-timeout: "PT5S"
1
java -Dcas.monitor.endpoints.ldap.response-timeout="PT5S" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_RESPONSE_TIMEOUT="PT5S"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.response-timeout="PT5S"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.sasl-authorization-id=
SASL authorization id.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.sasl-authorization-id
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.sasl-authorization-id=...
1
cas:
monitor:
endpoints:
ldap:
sasl-authorization-id: "..."
1
java -Dcas.monitor.endpoints.ldap.sasl-authorization-id="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SASL_AUTHORIZATION_ID="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.sasl-authorization-id="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.sasl-mechanism=
The SASL mechanism.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.sasl-mechanism
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.sasl-mechanism=...
1
cas:
monitor:
endpoints:
ldap:
sasl-mechanism: "..."
1
java -Dcas.monitor.endpoints.ldap.sasl-mechanism="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SASL_MECHANISM="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.sasl-mechanism="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.sasl-mutual-auth=
SASL mutual auth is enabled?
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.sasl-mutual-auth
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.sasl-mutual-auth=...
1
cas:
monitor:
endpoints:
ldap:
sasl-mutual-auth: "..."
1
java -Dcas.monitor.endpoints.ldap.sasl-mutual-auth="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SASL_MUTUAL_AUTH="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.sasl-mutual-auth="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.sasl-quality-of-protection=
SASL quality of protected.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.sasl-quality-of-protection
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.sasl-quality-of-protection=...
1
cas:
monitor:
endpoints:
ldap:
sasl-quality-of-protection: "..."
1
java -Dcas.monitor.endpoints.ldap.sasl-quality-of-protection="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SASL_QUALITY_OF_PROTECTION="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.sasl-quality-of-protection="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.sasl-realm=
The SASL realm.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.sasl-realm
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.sasl-realm=...
1
cas:
monitor:
endpoints:
ldap:
sasl-realm: "..."
1
java -Dcas.monitor.endpoints.ldap.sasl-realm="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SASL_REALM="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.sasl-realm="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.sasl-security-strength=
SASL security strength.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.sasl-security-strength
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.sasl-security-strength=...
1
cas:
monitor:
endpoints:
ldap:
sasl-security-strength: "..."
1
java -Dcas.monitor.endpoints.ldap.sasl-security-strength="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SASL_SECURITY_STRENGTH="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.sasl-security-strength="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers=
Search handlers.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.subtree-search=true
Whether subtree searching is allowed.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.subtree-search
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.subtree-search=true
1
cas:
monitor:
endpoints:
ldap:
subtree-search: "true"
1
java -Dcas.monitor.endpoints.ldap.subtree-search="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SUBTREE_SEARCH="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.subtree-search="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.trust-certificates=
Path of the trust certificates to use for the SSL connection. Ignores keystore-related settings when activated and used.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.trust-certificates
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.trust-certificates=...
1
cas:
monitor:
endpoints:
ldap:
trust-certificates: "..."
1
java -Dcas.monitor.endpoints.ldap.trust-certificates="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_TRUST_CERTIFICATES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.trust-certificates="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.trust-manager=
Trust Manager options. Trust managers are responsible for managing the trust material that is used when making LDAP trust decisions, and for deciding whether credentials presented by a peer should be accepted. Accepted values are: *
DEFAULT: Enable and force the default JVM trust managers.ANY: Trust any client or server.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.trust-manager
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.trust-manager=...
1
cas:
monitor:
endpoints:
ldap:
trust-manager: "..."
1
java -Dcas.monitor.endpoints.ldap.trust-manager="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_TRUST_MANAGER="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.trust-manager="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.trust-store=
Path to the keystore used to determine which certificates or certificate authorities should be trusted. Used when connecting to an LDAP server via LDAPS or startTLS connection. If left blank, the default truststore for the Java runtime is used.
This setting supports the Spring Expression Language.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.trust-store
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.trust-store=...
1
cas:
monitor:
endpoints:
ldap:
trust-store: "..."
1
java -Dcas.monitor.endpoints.ldap.trust-store="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_TRUST_STORE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.trust-store="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.trust-store-password=
Password needed to open the truststore.
This setting supports the Spring Expression Language.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.trust-store-password
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.trust-store-password=...
1
cas:
monitor:
endpoints:
ldap:
trust-store-password: "..."
1
java -Dcas.monitor.endpoints.ldap.trust-store-password="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_TRUST_STORE_PASSWORD="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.trust-store-password="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.trust-store-type=
The type of trust keystore that determines which certificates or certificate authorities are trusted. Types depend on underlying java platform, typically PKCS12 or JKS. If left blank, defaults to the default keystore type indicated by the underlying Java platform.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.trust-store-type
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.trust-store-type=...
1
cas:
monitor:
endpoints:
ldap:
trust-store-type: "..."
1
java -Dcas.monitor.endpoints.ldap.trust-store-type="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_TRUST_STORE_TYPE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.trust-store-type="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.use-start-tls=false
Whether TLS should be used and enabled when establishing the connection.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.use-start-tls
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.use-start-tls=...
1
cas:
monitor:
endpoints:
ldap:
use-start-tls: "..."
1
java -Dcas.monitor.endpoints.ldap.use-start-tls="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_USE_START_TLS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.use-start-tls="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validate-on-checkout=true
Whether connections should be validated when loaned out from the pool.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.validate-on-checkout
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validate-on-checkout=true
1
cas:
monitor:
endpoints:
ldap:
validate-on-checkout: "true"
1
java -Dcas.monitor.endpoints.ldap.validate-on-checkout="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATE_ON_CHECKOUT="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validate-on-checkout="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validate-period=PT5M
Period at which pool should be validated.
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.validate-period
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validate-period=PT5M
1
cas:
monitor:
endpoints:
ldap:
validate-period: "PT5M"
1
java -Dcas.monitor.endpoints.ldap.validate-period="PT5M" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATE_PERIOD="PT5M"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validate-period="PT5M"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validate-periodically=true
Whether connections should be validated periodically when the pool is idle.
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.validate-periodically
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validate-periodically=true
1
cas:
monitor:
endpoints:
ldap:
validate-periodically: "true"
1
java -Dcas.monitor.endpoints.ldap.validate-periodically="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATE_PERIODICALLY="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validate-periodically="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validate-timeout=PT5S
Period at which validation operations may time out.
This settings supports the
java.time.Duration syntax [?].
org.apereo.cas.configuration.model.core.monitor.LdapSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.ldap.validate-timeout
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validate-timeout=PT5S
1
cas:
monitor:
endpoints:
ldap:
validate-timeout: "PT5S"
1
java -Dcas.monitor.endpoints.ldap.validate-timeout="PT5S" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATE_TIMEOUT="PT5S"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validate-timeout="PT5S"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-authz.allow-multiple-results=false
Indicate whether the LDAP search query is allowed to return multiple entries.
org.apereo.cas.configuration.model.support.ldap.LdapAuthorizationProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-authz.allow-multiple-results
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-authz.allow-multiple-results=...
1
cas:
monitor:
endpoints:
ldap:
ldap-authz:
allow-multiple-results: "..."
1
java -Dcas.monitor.endpoints.ldap.ldap-authz.allow-multiple-results="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_AUTHZ_ALLOW_MULTIPLE_RESULTS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-authz.allow-multiple-results="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-authz.base-dn=
Base DN to start the search.
org.apereo.cas.configuration.model.support.ldap.LdapAuthorizationProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-authz.base-dn
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-authz.base-dn=...
1
cas:
monitor:
endpoints:
ldap:
ldap-authz:
base-dn: "..."
1
java -Dcas.monitor.endpoints.ldap.ldap-authz.base-dn="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_AUTHZ_BASE_DN="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-authz.base-dn="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-authz.group-attribute=
Attribute expected to be found on the entry resulting from the group search whose value is going to be used to construct roles. The final value is always prefixed with #groupPrefix. This is useful in scenarios where you wish to grant access to a resource to all users who a member of a given group.
org.apereo.cas.configuration.model.support.ldap.LdapAuthorizationProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-authz.group-attribute
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-authz.group-attribute=...
1
cas:
monitor:
endpoints:
ldap:
ldap-authz:
group-attribute: "..."
1
java -Dcas.monitor.endpoints.ldap.ldap-authz.group-attribute="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_AUTHZ_GROUP_ATTRIBUTE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-authz.group-attribute="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-authz.group-base-dn=
Base DN to start the search looking for groups.
org.apereo.cas.configuration.model.support.ldap.LdapAuthorizationProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-authz.group-base-dn
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-authz.group-base-dn=...
1
cas:
monitor:
endpoints:
ldap:
ldap-authz:
group-base-dn: "..."
1
java -Dcas.monitor.endpoints.ldap.ldap-authz.group-base-dn="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_AUTHZ_GROUP_BASE_DN="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-authz.group-base-dn="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-authz.group-filter=
Search filter to begin looking for groups.
org.apereo.cas.configuration.model.support.ldap.LdapAuthorizationProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-authz.group-filter
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-authz.group-filter=...
1
cas:
monitor:
endpoints:
ldap:
ldap-authz:
group-filter: "..."
1
java -Dcas.monitor.endpoints.ldap.ldap-authz.group-filter="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_AUTHZ_GROUP_FILTER="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-authz.group-filter="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-authz.group-prefix=
A prefix that is prepended to the group attribute value to construct an authorized role.
org.apereo.cas.configuration.model.support.ldap.LdapAuthorizationProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-authz.group-prefix
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-authz.group-prefix=...
1
cas:
monitor:
endpoints:
ldap:
ldap-authz:
group-prefix: "..."
1
java -Dcas.monitor.endpoints.ldap.ldap-authz.group-prefix="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_AUTHZ_GROUP_PREFIX="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-authz.group-prefix="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-authz.role-attribute=uugid
Attribute expected to be found on the entry whose value is going to be used to construct roles. The final value is always prefixed with #rolePrefix. This is useful in scenarios where you wish to grant access to a resource to all users who carry a special attribute.
org.apereo.cas.configuration.model.support.ldap.LdapAuthorizationProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-authz.role-attribute
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-authz.role-attribute=uugid
1
cas:
monitor:
endpoints:
ldap:
ldap-authz:
role-attribute: "uugid"
1
java -Dcas.monitor.endpoints.ldap.ldap-authz.role-attribute="uugid" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_AUTHZ_ROLE_ATTRIBUTE="uugid"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-authz.role-attribute="uugid"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-authz.role-prefix=ROLE_
Prefix for the role.
org.apereo.cas.configuration.model.support.ldap.LdapAuthorizationProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-authz.role-prefix
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-authz.role-prefix=ROLE_
1
cas:
monitor:
endpoints:
ldap:
ldap-authz:
role-prefix: "ROLE_"
1
java -Dcas.monitor.endpoints.ldap.ldap-authz.role-prefix="ROLE_" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_AUTHZ_ROLE_PREFIX="ROLE_"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-authz.role-prefix="ROLE_"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.ldap-authz.search-filter=
LDAP search filter to locate accounts.
org.apereo.cas.configuration.model.support.ldap.LdapAuthorizationProperties.
CAS Property: cas.monitor.endpoints.ldap.ldap-authz.search-filter
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.ldap-authz.search-filter=...
1
cas:
monitor:
endpoints:
ldap:
ldap-authz:
search-filter: "..."
1
java -Dcas.monitor.endpoints.ldap.ldap-authz.search-filter="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_LDAP_AUTHZ_SEARCH_FILTER="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.ldap-authz.search-filter="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-name-case-change=
The Attribute name case change.
org.apereo.cas.configuration.model.support.ldap.CaseChangeSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].case-change.attribute-name-case-change
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-name-case-change=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
case-change:
attribute-name-case-change: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-name-case-change="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_CASE_CHANGE_ATTRIBUTE_NAME_CASE_CHANGE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-name-case-change="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-names=
The Attribute names.
org.apereo.cas.configuration.model.support.ldap.CaseChangeSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].case-change.attribute-names
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-names=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
case-change:
attribute-names: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-names="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_CASE_CHANGE_ATTRIBUTE_NAMES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-names="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-value-case-change=
The Attribute value case change.
org.apereo.cas.configuration.model.support.ldap.CaseChangeSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].case-change.attribute-value-case-change
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-value-case-change=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
case-change:
attribute-value-case-change: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-value-case-change="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_CASE_CHANGE_ATTRIBUTE_VALUE_CASE_CHANGE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.attribute-value-case-change="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.dn-case-change=
The Dn case change.
org.apereo.cas.configuration.model.support.ldap.CaseChangeSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].case-change.dn-case-change
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.dn-case-change=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
case-change:
dn-case-change: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.dn-case-change="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_CASE_CHANGE_DN_CASE_CHANGE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].case-change.dn-case-change="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].dn-attribute.add-if-exists=
The Add if exists.
org.apereo.cas.configuration.model.support.ldap.DnAttributeSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].dn-attribute.add-if-exists
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].dn-attribute.add-if-exists=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
dn-attribute:
add-if-exists: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].dn-attribute.add-if-exists="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_DN_ATTRIBUTE_ADD_IF_EXISTS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].dn-attribute.add-if-exists="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].dn-attribute.dn-attribute-name=entryDN
The Dn attribute name.
org.apereo.cas.configuration.model.support.ldap.DnAttributeSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].dn-attribute.dn-attribute-name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].dn-attribute.dn-attribute-name=entryDN
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
dn-attribute:
dn-attribute-name: "entryDN"
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].dn-attribute.dn-attribute-name="entryDN" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_DN_ATTRIBUTE_DN_ATTRIBUTE_NAME="entryDN"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].dn-attribute.dn-attribute-name="entryDN"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].merge-attribute.attribute-names=
The Attribute names.
org.apereo.cas.configuration.model.support.ldap.MergeAttributesSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].merge-attribute.attribute-names
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].merge-attribute.attribute-names=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
merge-attribute:
attribute-names: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].merge-attribute.attribute-names="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_MERGE_ATTRIBUTE_ATTRIBUTE_NAMES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].merge-attribute.attribute-names="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].merge-attribute.merge-attribute-name=
The Merge attribute name.
org.apereo.cas.configuration.model.support.ldap.MergeAttributesSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].merge-attribute.merge-attribute-name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].merge-attribute.merge-attribute-name=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
merge-attribute:
merge-attribute-name: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].merge-attribute.merge-attribute-name="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_MERGE_ATTRIBUTE_MERGE_ATTRIBUTE_NAME="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].merge-attribute.merge-attribute-name="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].primary-group-id.base-dn=
The Base dn.
org.apereo.cas.configuration.model.support.ldap.PrimaryGroupIdSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].primary-group-id.base-dn
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].primary-group-id.base-dn=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
primary-group-id:
base-dn: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].primary-group-id.base-dn="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_PRIMARY_GROUP_ID_BASE_DN="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].primary-group-id.base-dn="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].primary-group-id.group-filter=(&(objectClass=group)(objectSid={0}))
The Group filter.
org.apereo.cas.configuration.model.support.ldap.PrimaryGroupIdSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].primary-group-id.group-filter
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].primary-group-id.group-filter=(&(objectClass=group)(objectSid={0}))
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
primary-group-id:
group-filter: "(&(objectClass=group)(objectSid={0}))"
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].primary-group-id.group-filter="(&(objectClass=group)(objectSid={0}))" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_PRIMARY_GROUP_ID_GROUP_FILTER="(&(objectClass=group)(objectSid={0}))"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].primary-group-id.group-filter="(&(objectClass=group)(objectSid={0}))"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].recursive.merge-attributes=
The Merge attributes.
org.apereo.cas.configuration.model.support.ldap.RecursiveSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].recursive.merge-attributes
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].recursive.merge-attributes=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
recursive:
merge-attributes: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].recursive.merge-attributes="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_RECURSIVE_MERGE_ATTRIBUTES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].recursive.merge-attributes="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].recursive.search-attribute=
The Search attribute.
org.apereo.cas.configuration.model.support.ldap.RecursiveSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].recursive.search-attribute
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].recursive.search-attribute=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
recursive:
search-attribute: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].recursive.search-attribute="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_RECURSIVE_SEARCH_ATTRIBUTE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].recursive.search-attribute="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].search-referral.limit=10
The default referral limit.
org.apereo.cas.configuration.model.support.ldap.FollowReferralSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].search-referral.limit
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].search-referral.limit=10
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
search-referral:
limit: "10"
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].search-referral.limit="10" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_SEARCH_REFERRAL_LIMIT="10"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].search-referral.limit="10"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].search-result.limit=10
The default referral limit.
org.apereo.cas.configuration.model.support.ldap.FollowResultSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].search-result.limit
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].search-result.limit=10
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
search-result:
limit: "10"
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].search-result.limit="10" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_SEARCH_RESULT_LIMIT="10"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].search-result.limit="10"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.search-entry-handlers[0].type=
The type of search entry handler to choose. Available values are as follows:
FOLLOW_SEARCH_REFERRAL: Provides handling of an ldap referral for search operations.FOLLOW_SEARCH_RESULT_REFERENCE: Provides handling of an ldap continuation reference for search operations.ACTIVE_DIRECTORY: Process the entry results fetched from active directory and check for account status controls for disabled/expired accounts, etc.OBJECT_GUID: Object guid search entry handler. Handles theobjectGUIDattribute fetching and conversion.OBJECT_SID: Object sid search entry handler. Handles theobjectSidattribute fetching and conversion.CASE_CHANGE: Case change search entry handler. Provides the ability to modify the case of search entry DNs, attribute names, and attribute values.DN_ATTRIBUTE_ENTRY: DN attribute entry handler. Adds the entry DN as an attribute to the result set. Provides a client side implementation of RFC 5020.MERGE: Merge search entry handler. Merges the values of one or more attributes into a single attribute.PRIMARY_GROUP: Primary group search handler. Constructs the primary group SID and then searches for that group and puts it's DN in thememberOfattribute of the original search entry.RANGE_ENTRY: Range entry search handler. Rewrites attributes returned from Active Directory to include all values by performing additional searches.RECURSIVE_ENTRY: Recursive entry search handler. This recursively searches based on a supplied attribute and merges those results into the original entry.MERGE_ENTRIES: Merge entries handler. Merges the values of one or more attributes in all entries into a single attribute. The merged attribute may or may not already exist on the entry. If it does exist it's existing values will remain intact.
org.apereo.cas.configuration.model.support.ldap.LdapSearchEntryHandlersProperties.
CAS Property: cas.monitor.endpoints.ldap.search-entry-handlers[].type
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.search-entry-handlers[0].type=...
1
cas:
monitor:
endpoints:
ldap:
search-entry-handlers[0]:
type: "..."
1
java -Dcas.monitor.endpoints.ldap.search-entry-handlers[0].type="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_SEARCH_ENTRY_HANDLERS[0]_TYPE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.search-entry-handlers[0].type="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validator.attribute-name=objectClass
Attribute name to use for the compare validator.
org.apereo.cas.configuration.model.support.ldap.LdapValidatorProperties.
CAS Property: cas.monitor.endpoints.ldap.validator.attribute-name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validator.attribute-name=objectClass
1
cas:
monitor:
endpoints:
ldap:
validator:
attribute-name: "objectClass"
1
java -Dcas.monitor.endpoints.ldap.validator.attribute-name="objectClass" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATOR_ATTRIBUTE_NAME="objectClass"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validator.attribute-name="objectClass"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validator.attribute-value=top
Attribute values to use for the compare validator.
org.apereo.cas.configuration.model.support.ldap.LdapValidatorProperties.
CAS Property: cas.monitor.endpoints.ldap.validator.attribute-value
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validator.attribute-value=top
1
cas:
monitor:
endpoints:
ldap:
validator:
attribute-value: "top"
1
java -Dcas.monitor.endpoints.ldap.validator.attribute-value="top" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATOR_ATTRIBUTE_VALUE="top"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validator.attribute-value="top"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validator.base-dn=
Base DN to use for the search request of the search validator.
org.apereo.cas.configuration.model.support.ldap.LdapValidatorProperties.
CAS Property: cas.monitor.endpoints.ldap.validator.base-dn
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validator.base-dn=...
1
cas:
monitor:
endpoints:
ldap:
validator:
base-dn: "..."
1
java -Dcas.monitor.endpoints.ldap.validator.base-dn="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATOR_BASE_DN="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validator.base-dn="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validator.dn=
DN to compare to use for the compare validator.
org.apereo.cas.configuration.model.support.ldap.LdapValidatorProperties.
CAS Property: cas.monitor.endpoints.ldap.validator.dn
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validator.dn=...
1
cas:
monitor:
endpoints:
ldap:
validator:
dn: "..."
1
java -Dcas.monitor.endpoints.ldap.validator.dn="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATOR_DN="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validator.dn="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validator.scope=OBJECT
Search scope to use for the search request of the search validator.
org.apereo.cas.configuration.model.support.ldap.LdapValidatorProperties.
CAS Property: cas.monitor.endpoints.ldap.validator.scope
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validator.scope=OBJECT
1
cas:
monitor:
endpoints:
ldap:
validator:
scope: "OBJECT"
1
java -Dcas.monitor.endpoints.ldap.validator.scope="OBJECT" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATOR_SCOPE="OBJECT"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validator.scope="OBJECT"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validator.search-filter=(objectClass=*)
Search filter to use for the search request of the search validator.
org.apereo.cas.configuration.model.support.ldap.LdapValidatorProperties.
CAS Property: cas.monitor.endpoints.ldap.validator.search-filter
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validator.search-filter=(objectClass=*)
1
cas:
monitor:
endpoints:
ldap:
validator:
search-filter: "(objectClass=*)"
1
java -Dcas.monitor.endpoints.ldap.validator.search-filter="(objectClass=*)" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATOR_SEARCH_FILTER="(objectClass=*)"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validator.search-filter="(objectClass=*)"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.ldap.validator.type=search
Determine the LDAP validator type.
The following LDAP validators can be used to test connection health status:search: Validates a connection is healthy by performing a search operation. Validation is considered successful if the search result size is greater than zero.none: No validation takes place.compare: Validates a connection is healthy by performing a compare operation.
org.apereo.cas.configuration.model.support.ldap.LdapValidatorProperties.
CAS Property: cas.monitor.endpoints.ldap.validator.type
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.ldap.validator.type=search
1
cas:
monitor:
endpoints:
ldap:
validator:
type: "search"
1
java -Dcas.monitor.endpoints.ldap.validator.type="search" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_LDAP_VALIDATOR_TYPE="search"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.ldap.validator.type="search"
cas.war
with an embedded server container and can be found in the build/libs directory.
LDAP Scriptable Search Filter
LDAP search filters can point to an external Groovy script to dynamically construct the final filter template.
The script itself may be designed as:
1
2
3
4
5
6
7
8
9
10
11
12
import org.ldaptive.*
import org.springframework.context.*
def run(Object[] args) {
def filter = (FilterTemplate) args[0]
def parameters = (Map) args[1]
def applicationContext = (ApplicationContext) args[2]
def logger = args[3]
logger.info("Configuring LDAP filter")
filter.setFilter("uid=something")
}
The following parameters are passed to the script:
| Parameter | Description |
|---|---|
filter |
FilterTemplate to be updated by the script and used for the LDAP query. |
parameters |
Map of query parameters which may be used to construct the final filter. |
applicationContext |
Reference to the Spring ApplicationContext reference. |
logger |
The object responsible for issuing log messages such as logger.info(...). |
The following settings and properties are available from the CAS configuration catalog:
- Required
- Optional
- Signing & Encryption
- Hibernate & JDBC
- Email Servers
- LDAP & Active Directory
- Authentication
- Password Encoding
- Principal Transformation
- Password Policy
cas.monitor.endpoints.jaas.login-config=
JAAS login resource file.
CAS Property:
|
1 | cas.monitor.endpoints.jaas.login-config=... |
1
cas:
monitor:
endpoints:
jaas:
login-config: "..."
1
java -Dcas.monitor.endpoints.jaas.login-config="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JAAS_LOGIN_CONFIG="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jaas.login-config="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jaas.login-context-name=
The login context name should coincide with a given index in the login config specified. This name is used as the index to the configuration specified in the login config property.
JAASTest { org.springframework.security.authentication.jaas.TestLoginModule required; }; In the above example, JAASTest should be set as the context name.
org.apereo.cas.configuration.model.core.monitor.JaasSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jaas.login-context-name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jaas.login-context-name=...
1
cas:
monitor:
endpoints:
jaas:
login-context-name: "..."
1
java -Dcas.monitor.endpoints.jaas.login-context-name="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JAAS_LOGIN_CONTEXT_NAME="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jaas.login-context-name="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.jaas.refresh-configuration-on-startup=true
If set, a call to Configuration#refresh() will be made by #configureJaas(Resource) method.
org.apereo.cas.configuration.model.core.monitor.JaasSecurityActuatorEndpointsMonitorProperties.
CAS Property: cas.monitor.endpoints.jaas.refresh-configuration-on-startup
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.jaas.refresh-configuration-on-startup=true
1
cas:
monitor:
endpoints:
jaas:
refresh-configuration-on-startup: "true"
1
java -Dcas.monitor.endpoints.jaas.refresh-configuration-on-startup="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_JAAS_REFRESH_CONFIGURATION_ON_STARTUP="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.jaas.refresh-configuration-on-startup="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
Get public key for signing operations.
Endpoint Details: jwtTicketSigningPublicKey
Endpoint Parameters:
-
service
CAS, being a Spring-Boot application at heart, includes a number of endpoints to help you monitor and manage the server when it’s pushed to production. You can choose to manage and monitor the deployment using HTTP endpoints, referred to as actuators.
In essence, actuator endpoints bring production-ready features to CAS. Monitoring a running CAS instance, gathering metrics, understanding traffic or the state of our database becomes trivial with such endpoints. The main benefit of these endpoints is that we can get production grade tools without having to actually implement these features ourselves. Actuators are mainly used to expose operational information about the running application – health, metrics, etc. These are HTTP endpoints or JMX beans to enable us to interact with it.
Actuator endpoints are presented by CAS in two categories:
- Those that are owned and defined by the CAS project.
- Those that are owned and defined by third-party projects, frameworks and libraries such as Spring Boot.
Note that by default the only endpoints exposed over the web
are info, status, health and configurationMetadata.
Other endpoints need to be explicitly enabled and then
exposed over the web in CAS settings in order to allow access.
To enable and expose an actuator endpoint:
1
2
3
4
5
management.endpoint.jwtTicketSigningPublicKey.enabled=true
management.endpoints.web.exposure.include=jwtTicketSigningPublicKey
# Choose the proper security access level...
# cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.access=PERMIT
The following settings and properties are available from the CAS configuration catalog:
- Required
- Optional
- Signing & Encryption
- Hibernate & JDBC
- Email Servers
- LDAP & Active Directory
- Authentication
- Password Encoding
- Principal Transformation
- Password Policy
cas.monitor.endpoints.form-login-enabled=false
Control whether access to endpoints can be controlled via form-based login over the web via a special admin login endpoint.
CAS Property:
|
1 | cas.monitor.endpoints.form-login-enabled=... |
1
cas:
monitor:
endpoints:
form-login-enabled: "..."
1
java -Dcas.monitor.endpoints.form-login-enabled="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_FORM_LOGIN_ENABLED="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.form-login-enabled="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.access=
Define the security access level of the endpoint. Available values are as follows:
PERMIT: Allow open access to the endpoint.ANONYMOUS: Allow anonymous access to the endpoint.DENY: Block access to the endpoint.AUTHENTICATED: Require authenticated access to the endpoint.ROLE: Require authenticated access to the endpoint along with a role requirement.AUTHORITY: Require authenticated access to the endpoint along with an authority requirement.IP_ADDRESS: Require authenticated access to the endpoint using a collection of IP addresses.
org.apereo.cas.configuration.model.core.monitor.ActuatorEndpointProperties.
CAS Property: cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.access
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.access=...
1
cas:
monitor:
endpoints:
endpoint:
jwtTicketSigningPublicKey:
access: "..."
1
java -Dcas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.access="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_ENDPOINT_[KEY]_ACCESS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.access="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-authorities=
Required user authorities.
org.apereo.cas.configuration.model.core.monitor.ActuatorEndpointProperties.
CAS Property: cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-authorities
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-authorities=...
1
cas:
monitor:
endpoints:
endpoint:
jwtTicketSigningPublicKey:
required-authorities: "..."
1
java -Dcas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-authorities="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_ENDPOINT_[KEY]_REQUIRED_AUTHORITIES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-authorities="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-ip-addresses=
Required ip addresses.
org.apereo.cas.configuration.model.core.monitor.ActuatorEndpointProperties.
CAS Property: cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-ip-addresses
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-ip-addresses=...
1
cas:
monitor:
endpoints:
endpoint:
jwtTicketSigningPublicKey:
required-ip-addresses: "..."
1
java -Dcas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-ip-addresses="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_ENDPOINT_[KEY]_REQUIRED_IP_ADDRESSES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-ip-addresses="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-roles=
Required user roles.
org.apereo.cas.configuration.model.core.monitor.ActuatorEndpointProperties.
CAS Property: cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-roles
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-roles=...
1
cas:
monitor:
endpoints:
endpoint:
jwtTicketSigningPublicKey:
required-roles: "..."
1
java -Dcas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-roles="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_MONITOR_ENDPOINTS_ENDPOINT_[KEY]_REQUIRED_ROLES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.monitor.endpoints.endpoint.jwtTicketSigningPublicKey.required-roles="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
Endpoints may be mapped to custom arbitrary endpoints. For example,
to remap the health endpoint to healthcheck,
specify the following settings:
1
management.endpoints.web.path-mapping.health=healthcheck
management.endpoint.health.cache.time-to-live=0ms
Maximum time that a response can be cached.
CAS Property:
|
1 | management.endpoint.health.cache.time-to-live=0ms |
1
management:
endpoint:
health:
cache:
time-to-live: "0ms"
1
java -Dmanagement.endpoint.health.cache.time-to-live="0ms" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_CACHE_TIME_TO_LIVE="0ms"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.cache.time-to-live="0ms"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.enabled=true
Whether to enable the health endpoint.
org.springframework.boot.actuate.health.HealthEndpoint.
CAS Property: management.endpoint.health.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.enabled=true
1
management:
endpoint:
health:
enabled: "true"
1
java -Dmanagement.endpoint.health.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.group=
Health endpoint groups.
org.springframework.boot.actuate.autoconfigure.health.HealthEndpointProperties.
CAS Property: management.endpoint.health.group
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.group=...
1
management:
endpoint:
health:
group: "..."
1
java -Dmanagement.endpoint.health.group="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_GROUP="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.group="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.logging.slow-indicator-threshold=10s
Threshold after which a warning will be logged for slow health indicators.
org.springframework.boot.actuate.autoconfigure.health.HealthEndpointProperties$Logging.
CAS Property: management.endpoint.health.logging.slow-indicator-threshold
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.logging.slow-indicator-threshold=10s
1
management:
endpoint:
health:
logging:
slow-indicator-threshold: "10s"
1
java -Dmanagement.endpoint.health.logging.slow-indicator-threshold="10s" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_LOGGING_SLOW_INDICATOR_THRESHOLD="10s"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.logging.slow-indicator-threshold="10s"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.probes.add-additional-paths=false
Whether to make the liveness and readiness health groups available on the main server port.
How can I configure this property?
CAS Property: management.endpoint.health.probes.add-additional-paths
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.probes.add-additional-paths=...
1
management:
endpoint:
health:
probes:
add-additional-paths: "..."
1
java -Dmanagement.endpoint.health.probes.add-additional-paths="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_PROBES_ADD_ADDITIONAL_PATHS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.probes.add-additional-paths="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.probes.enabled=false
Whether to enable liveness and readiness probes.
How can I configure this property?
CAS Property: management.endpoint.health.probes.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.probes.enabled=...
1
management:
endpoint:
health:
probes:
enabled: "..."
1
java -Dmanagement.endpoint.health.probes.enabled="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_PROBES_ENABLED="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.probes.enabled="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.roles=
Roles used to determine whether a user is authorized to be shown details. When empty, all authenticated users are authorized.
org.springframework.boot.actuate.autoconfigure.health.HealthEndpointProperties.
CAS Property: management.endpoint.health.roles
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.roles=...
1
management:
endpoint:
health:
roles: "..."
1
java -Dmanagement.endpoint.health.roles="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_ROLES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.roles="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.show-components=
When to show components. If not specified the 'show-details' setting will be used.
org.springframework.boot.actuate.autoconfigure.health.HealthEndpointProperties.
CAS Property: management.endpoint.health.show-components
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.show-components=...
1
management:
endpoint:
health:
show-components: "..."
1
java -Dmanagement.endpoint.health.show-components="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_SHOW_COMPONENTS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.show-components="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.show-details=never
When to show full health details.
org.springframework.boot.actuate.autoconfigure.health.HealthEndpointProperties.
CAS Property: management.endpoint.health.show-details
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.show-details=never
1
management:
endpoint:
health:
show-details: "never"
1
java -Dmanagement.endpoint.health.show-details="never" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_SHOW_DETAILS="never"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.show-details="never"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.status.http-mapping=
Mapping of health statuses to HTTP status codes. By default, registered health statuses map to sensible defaults (for example, UP maps to 200).
org.springframework.boot.actuate.autoconfigure.health.HealthProperties$Status.
CAS Property: management.endpoint.health.status.http-mapping
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.status.http-mapping=...
1
management:
endpoint:
health:
status:
http-mapping: "..."
1
java -Dmanagement.endpoint.health.status.http-mapping="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_STATUS_HTTP_MAPPING="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.status.http-mapping="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoint.health.status.order=DOWNOUT_OF_SERVICEUPUNKNOWN
Comma-separated list of health statuses in order of severity.
org.springframework.boot.actuate.autoconfigure.health.HealthProperties$Status.
CAS Property: management.endpoint.health.status.order
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoint.health.status.order=DOWNOUT_OF_SERVICEUPUNKNOWN
1
management:
endpoint:
health:
status:
order: "["DOWN", "OUT_OF_SERVICE", "UP", "UNKNOWN"]"
1
java -Dmanagement.endpoint.health.status.order="["DOWN", "OUT_OF_SERVICE", "UP", "UNKNOWN"]" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINT_HEALTH_STATUS_ORDER="["DOWN", "OUT_OF_SERVICE", "UP", "UNKNOWN"]"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoint.health.status.order="["DOWN", "OUT_OF_SERVICE", "UP", "UNKNOWN"]"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.enabled-by-default=
Whether to enable or disable all endpoints by default.
How can I configure this property?
CAS Property: management.endpoints.enabled-by-default
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.enabled-by-default=...
1
management:
endpoints:
enabled-by-default: "..."
1
java -Dmanagement.endpoints.enabled-by-default="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_ENABLED_BY_DEFAULT="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.enabled-by-default="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.jmx.domain=org.springframework.boot
Endpoints JMX domain name. Fallback to 'spring.jmx.default-domain' if set.
org.springframework.boot.actuate.autoconfigure.endpoint.jmx.JmxEndpointProperties.
CAS Property: management.endpoints.jmx.domain
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.jmx.domain=org.springframework.boot
1
management:
endpoints:
jmx:
domain: "org.springframework.boot"
1
java -Dmanagement.endpoints.jmx.domain="org.springframework.boot" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_JMX_DOMAIN="org.springframework.boot"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.jmx.domain="org.springframework.boot"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.jmx.exposure.exclude=
Endpoint IDs that should be excluded or '*' for all.
org.springframework.boot.actuate.autoconfigure.endpoint.jmx.JmxEndpointProperties$Exposure.
CAS Property: management.endpoints.jmx.exposure.exclude
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.jmx.exposure.exclude=...
1
management:
endpoints:
jmx:
exposure:
exclude: "..."
1
java -Dmanagement.endpoints.jmx.exposure.exclude="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_JMX_EXPOSURE_EXCLUDE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.jmx.exposure.exclude="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.jmx.exposure.include=*
Endpoint IDs that should be included or '*' for all.
org.springframework.boot.actuate.autoconfigure.endpoint.jmx.JmxEndpointProperties$Exposure.
CAS Property: management.endpoints.jmx.exposure.include
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.jmx.exposure.include=*
1
management:
endpoints:
jmx:
exposure:
include: "*"
1
java -Dmanagement.endpoints.jmx.exposure.include="*" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_JMX_EXPOSURE_INCLUDE="*"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.jmx.exposure.include="*"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.jmx.static-names=
Additional static properties to append to all ObjectNames of MBeans representing Endpoints.
org.springframework.boot.actuate.autoconfigure.endpoint.jmx.JmxEndpointProperties.
CAS Property: management.endpoints.jmx.static-names
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.jmx.static-names=...
1
management:
endpoints:
jmx:
static-names: "..."
1
java -Dmanagement.endpoints.jmx.static-names="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_JMX_STATIC_NAMES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.jmx.static-names="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.jmx.unique-names=
Whether unique runtime object names should be ensured.
How can I configure this property?
CAS Property: management.endpoints.jmx.unique-names
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.jmx.unique-names=...
1
management:
endpoints:
jmx:
unique-names: "..."
1
java -Dmanagement.endpoints.jmx.unique-names="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_JMX_UNIQUE_NAMES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.jmx.unique-names="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
Deprecation status is ERRORwith a replacement setting: spring.jmx.unique-names.
management.endpoints.migrate-legacy-ids=false
Whether to transparently migrate legacy endpoint IDs.
How can I configure this property?
CAS Property: management.endpoints.migrate-legacy-ids
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.migrate-legacy-ids=...
1
management:
endpoints:
migrate-legacy-ids: "..."
1
java -Dmanagement.endpoints.migrate-legacy-ids="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_MIGRATE_LEGACY_IDS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.migrate-legacy-ids="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.base-path=/actuator
Base path for Web endpoints. Relative to the servlet context path (server.servlet.context-path) or WebFlux base path (spring.webflux.base-path) when the management server is sharing the main server port. Relative to the management server base path (management.server.base-path) when a separate management server port (management.server.port) is configured.
org.springframework.boot.actuate.autoconfigure.endpoint.web.WebEndpointProperties.
CAS Property: management.endpoints.web.base-path
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.base-path=/actuator
1
management:
endpoints:
web:
base-path: "/actuator"
1
java -Dmanagement.endpoints.web.base-path="/actuator" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_BASE_PATH="/actuator"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.base-path="/actuator"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.cors.allow-credentials=
Whether credentials are supported. When not set, credentials are not supported.
org.springframework.boot.actuate.autoconfigure.endpoint.web.CorsEndpointProperties.
CAS Property: management.endpoints.web.cors.allow-credentials
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.cors.allow-credentials=...
1
management:
endpoints:
web:
cors:
allow-credentials: "..."
1
java -Dmanagement.endpoints.web.cors.allow-credentials="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_CORS_ALLOW_CREDENTIALS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.cors.allow-credentials="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.cors.allowed-headers=
Comma-separated list of headers to allow in a request. '*' allows all headers.
org.springframework.boot.actuate.autoconfigure.endpoint.web.CorsEndpointProperties.
CAS Property: management.endpoints.web.cors.allowed-headers
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.cors.allowed-headers=...
1
management:
endpoints:
web:
cors:
allowed-headers: "..."
1
java -Dmanagement.endpoints.web.cors.allowed-headers="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_CORS_ALLOWED_HEADERS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.cors.allowed-headers="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.cors.allowed-methods=
Comma-separated list of methods to allow. '*' allows all methods. When not set, defaults to GET.
org.springframework.boot.actuate.autoconfigure.endpoint.web.CorsEndpointProperties.
CAS Property: management.endpoints.web.cors.allowed-methods
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.cors.allowed-methods=...
1
management:
endpoints:
web:
cors:
allowed-methods: "..."
1
java -Dmanagement.endpoints.web.cors.allowed-methods="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_CORS_ALLOWED_METHODS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.cors.allowed-methods="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.cors.allowed-origin-patterns=
Comma-separated list of origin patterns to allow. Unlike allowed origins which only supports '*', origin patterns are more flexible (for example 'https://*.example.com') and can be used when credentials are allowed. When no allowed origin patterns or allowed origins are set, CORS support is disabled.
org.springframework.boot.actuate.autoconfigure.endpoint.web.CorsEndpointProperties.
CAS Property: management.endpoints.web.cors.allowed-origin-patterns
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.cors.allowed-origin-patterns=...
1
management:
endpoints:
web:
cors:
allowed-origin-patterns: "..."
1
java -Dmanagement.endpoints.web.cors.allowed-origin-patterns="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_CORS_ALLOWED_ORIGIN_PATTERNS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.cors.allowed-origin-patterns="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.cors.allowed-origins=
Comma-separated list of origins to allow. '*' allows all origins. When credentials are allowed, '*' cannot be used and origin patterns should be configured instead. When no allowed origins or allowed origin patterns are set, CORS support is disabled.
org.springframework.boot.actuate.autoconfigure.endpoint.web.CorsEndpointProperties.
CAS Property: management.endpoints.web.cors.allowed-origins
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.cors.allowed-origins=...
1
management:
endpoints:
web:
cors:
allowed-origins: "..."
1
java -Dmanagement.endpoints.web.cors.allowed-origins="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_CORS_ALLOWED_ORIGINS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.cors.allowed-origins="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.cors.exposed-headers=
Comma-separated list of headers to include in a response.
org.springframework.boot.actuate.autoconfigure.endpoint.web.CorsEndpointProperties.
CAS Property: management.endpoints.web.cors.exposed-headers
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.cors.exposed-headers=...
1
management:
endpoints:
web:
cors:
exposed-headers: "..."
1
java -Dmanagement.endpoints.web.cors.exposed-headers="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_CORS_EXPOSED_HEADERS="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.cors.exposed-headers="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.cors.max-age=1800s
How long the response from a pre-flight request can be cached by clients. If a duration suffix is not specified, seconds will be used.
org.springframework.boot.actuate.autoconfigure.endpoint.web.CorsEndpointProperties.
CAS Property: management.endpoints.web.cors.max-age
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.cors.max-age=1800s
1
management:
endpoints:
web:
cors:
max-age: "1800s"
1
java -Dmanagement.endpoints.web.cors.max-age="1800s" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_CORS_MAX_AGE="1800s"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.cors.max-age="1800s"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.discovery.enabled=true
Whether the discovery page is enabled.
org.springframework.boot.actuate.autoconfigure.endpoint.web.WebEndpointProperties$Discovery.
CAS Property: management.endpoints.web.discovery.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.discovery.enabled=true
1
management:
endpoints:
web:
discovery:
enabled: "true"
1
java -Dmanagement.endpoints.web.discovery.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_DISCOVERY_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.discovery.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.exposure.exclude=
Endpoint IDs that should be excluded or '*' for all.
org.springframework.boot.actuate.autoconfigure.endpoint.web.WebEndpointProperties$Exposure.
CAS Property: management.endpoints.web.exposure.exclude
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.exposure.exclude=...
1
management:
endpoints:
web:
exposure:
exclude: "..."
1
java -Dmanagement.endpoints.web.exposure.exclude="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_EXPOSURE_EXCLUDE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.exposure.exclude="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.exposure.include=health
Endpoint IDs that should be included or '*' for all.
org.springframework.boot.actuate.autoconfigure.endpoint.web.WebEndpointProperties$Exposure.
CAS Property: management.endpoints.web.exposure.include
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.exposure.include=health
1
management:
endpoints:
web:
exposure:
include: "["health"]"
1
java -Dmanagement.endpoints.web.exposure.include="["health"]" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_EXPOSURE_INCLUDE="["health"]"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.exposure.include="["health"]"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.endpoints.web.path-mapping=
Mapping between endpoint IDs and the path that should expose them.
org.springframework.boot.actuate.autoconfigure.endpoint.web.WebEndpointProperties.
CAS Property: management.endpoints.web.path-mapping
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.endpoints.web.path-mapping=...
1
management:
endpoints:
web:
path-mapping: "..."
1
java -Dmanagement.endpoints.web.path-mapping="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_ENDPOINTS_WEB_PATH_MAPPING="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.endpoints.web.path-mapping="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.binders.enabled=true
Allows to enable/disable binder's' health indicators. If you want to disable health indicator completely, then set it to `false`.
How can I configure this property?
CAS Property: management.health.binders.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.binders.enabled=true
1
management:
health:
binders:
enabled: "true"
1
java -Dmanagement.health.binders.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_BINDERS_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.binders.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.cassandra.enabled=true
Whether to enable Cassandra health check.
How can I configure this property?
CAS Property: management.health.cassandra.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.cassandra.enabled=true
1
management:
health:
cassandra:
enabled: "true"
1
java -Dmanagement.health.cassandra.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_CASSANDRA_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.cassandra.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.couchbase.enabled=true
Whether to enable Couchbase health check.
How can I configure this property?
CAS Property: management.health.couchbase.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.couchbase.enabled=true
1
management:
health:
couchbase:
enabled: "true"
1
java -Dmanagement.health.couchbase.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_COUCHBASE_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.couchbase.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.couchbase.timeout=1000ms
Timeout for getting the Bucket information from the server.
How can I configure this property?
CAS Property: management.health.couchbase.timeout
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.couchbase.timeout=1000ms
1
management:
health:
couchbase:
timeout: "1000ms"
1
java -Dmanagement.health.couchbase.timeout="1000ms" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_COUCHBASE_TIMEOUT="1000ms"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.couchbase.timeout="1000ms"
cas.war
with an embedded server container and can be found in the build/libs directory.
Deprecation status is ERRORwithout a replacement setting.
management.health.db.enabled=true
Whether to enable database health check.
How can I configure this property?
CAS Property: management.health.db.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.db.enabled=true
1
management:
health:
db:
enabled: "true"
1
java -Dmanagement.health.db.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_DB_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.db.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.db.ignore-routing-data-sources=false
Whether to ignore AbstractRoutingDataSources when creating database health indicators.
org.springframework.boot.actuate.autoconfigure.jdbc.DataSourceHealthIndicatorProperties.
CAS Property: management.health.db.ignore-routing-data-sources
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.db.ignore-routing-data-sources=...
1
management:
health:
db:
ignore-routing-data-sources: "..."
1
java -Dmanagement.health.db.ignore-routing-data-sources="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_DB_IGNORE_ROUTING_DATA_SOURCES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.db.ignore-routing-data-sources="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.defaults.enabled=true
Whether to enable default health indicators.
How can I configure this property?
CAS Property: management.health.defaults.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.defaults.enabled=true
1
management:
health:
defaults:
enabled: "true"
1
java -Dmanagement.health.defaults.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_DEFAULTS_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.defaults.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.diskspace.enabled=true
Whether to enable disk space health check.
How can I configure this property?
CAS Property: management.health.diskspace.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.diskspace.enabled=true
1
management:
health:
diskspace:
enabled: "true"
1
java -Dmanagement.health.diskspace.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_DISKSPACE_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.diskspace.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.diskspace.path=
Path used to compute the available disk space.
org.springframework.boot.actuate.autoconfigure.system.DiskSpaceHealthIndicatorProperties.
CAS Property: management.health.diskspace.path
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.diskspace.path=...
1
management:
health:
diskspace:
path: "..."
1
java -Dmanagement.health.diskspace.path="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_DISKSPACE_PATH="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.diskspace.path="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.diskspace.threshold=10MB
Minimum disk space that should be available.
org.springframework.boot.actuate.autoconfigure.system.DiskSpaceHealthIndicatorProperties.
CAS Property: management.health.diskspace.threshold
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.diskspace.threshold=10MB
1
management:
health:
diskspace:
threshold: "10MB"
1
java -Dmanagement.health.diskspace.threshold="10MB" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_DISKSPACE_THRESHOLD="10MB"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.diskspace.threshold="10MB"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.elasticsearch.enabled=true
Whether to enable Elasticsearch health check.
How can I configure this property?
CAS Property: management.health.elasticsearch.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.elasticsearch.enabled=true
1
management:
health:
elasticsearch:
enabled: "true"
1
java -Dmanagement.health.elasticsearch.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_ELASTICSEARCH_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.elasticsearch.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.elasticsearch.indices=
Comma-separated index names.
How can I configure this property?
CAS Property: management.health.elasticsearch.indices
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.elasticsearch.indices=...
1
management:
health:
elasticsearch:
indices: "..."
1
java -Dmanagement.health.elasticsearch.indices="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_ELASTICSEARCH_INDICES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.elasticsearch.indices="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
Deprecation status is ERRORwithout a replacement setting.
management.health.elasticsearch.response-timeout=
Time to wait for a response from the cluster.
How can I configure this property?
CAS Property: management.health.elasticsearch.response-timeout
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.elasticsearch.response-timeout=...
1
management:
health:
elasticsearch:
response-timeout: "..."
1
java -Dmanagement.health.elasticsearch.response-timeout="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_ELASTICSEARCH_RESPONSE_TIMEOUT="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.elasticsearch.response-timeout="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
Deprecation status is ERRORwithout a replacement setting.
management.health.influxdb.enabled=true
Whether to enable InfluxDB health check.
How can I configure this property?
CAS Property: management.health.influxdb.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.influxdb.enabled=true
1
management:
health:
influxdb:
enabled: "true"
1
java -Dmanagement.health.influxdb.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_INFLUXDB_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.influxdb.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.jms.enabled=true
Whether to enable JMS health check.
How can I configure this property?
CAS Property: management.health.jms.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.jms.enabled=true
1
management:
health:
jms:
enabled: "true"
1
java -Dmanagement.health.jms.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_JMS_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.jms.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.ldap.enabled=true
Whether to enable LDAP health check.
How can I configure this property?
CAS Property: management.health.ldap.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.ldap.enabled=true
1
management:
health:
ldap:
enabled: "true"
1
java -Dmanagement.health.ldap.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_LDAP_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.ldap.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.livenessstate.enabled=false
Whether to enable liveness state health check.
How can I configure this property?
CAS Property: management.health.livenessstate.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.livenessstate.enabled=...
1
management:
health:
livenessstate:
enabled: "..."
1
java -Dmanagement.health.livenessstate.enabled="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_LIVENESSSTATE_ENABLED="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.livenessstate.enabled="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.mail.enabled=true
Whether to enable Mail health check.
How can I configure this property?
CAS Property: management.health.mail.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.mail.enabled=true
1
management:
health:
mail:
enabled: "true"
1
java -Dmanagement.health.mail.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_MAIL_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.mail.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.mongo.enabled=true
Whether to enable MongoDB health check.
How can I configure this property?
CAS Property: management.health.mongo.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.mongo.enabled=true
1
management:
health:
mongo:
enabled: "true"
1
java -Dmanagement.health.mongo.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_MONGO_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.mongo.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.neo4j.enabled=true
Whether to enable Neo4j health check.
How can I configure this property?
CAS Property: management.health.neo4j.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.neo4j.enabled=true
1
management:
health:
neo4j:
enabled: "true"
1
java -Dmanagement.health.neo4j.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_NEO4J_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.neo4j.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.ping.enabled=true
Whether to enable ping health check.
How can I configure this property?
CAS Property: management.health.ping.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.ping.enabled=true
1
management:
health:
ping:
enabled: "true"
1
java -Dmanagement.health.ping.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_PING_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.ping.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.probes.enabled=false
Whether to enable liveness and readiness probes.
How can I configure this property?
CAS Property: management.health.probes.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.probes.enabled=...
1
management:
health:
probes:
enabled: "..."
1
java -Dmanagement.health.probes.enabled="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_PROBES_ENABLED="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.probes.enabled="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
Deprecation status is WARNINGwith a replacement setting: management.endpoint.health.probes.enabled.
management.health.rabbit.enabled=true
Whether to enable RabbitMQ health check.
How can I configure this property?
CAS Property: management.health.rabbit.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.rabbit.enabled=true
1
management:
health:
rabbit:
enabled: "true"
1
java -Dmanagement.health.rabbit.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_RABBIT_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.rabbit.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.readinessstate.enabled=false
Whether to enable readiness state health check.
How can I configure this property?
CAS Property: management.health.readinessstate.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.readinessstate.enabled=...
1
management:
health:
readinessstate:
enabled: "..."
1
java -Dmanagement.health.readinessstate.enabled="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_READINESSSTATE_ENABLED="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.readinessstate.enabled="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.redis.enabled=true
Whether to enable Redis health check.
How can I configure this property?
CAS Property: management.health.redis.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.redis.enabled=true
1
management:
health:
redis:
enabled: "true"
1
java -Dmanagement.health.redis.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_REDIS_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.redis.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.refresh.enabled=true
Enable the health endpoint for the refresh scope.
How can I configure this property?
CAS Property: management.health.refresh.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.refresh.enabled=true
1
management:
health:
refresh:
enabled: "true"
1
java -Dmanagement.health.refresh.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_REFRESH_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.refresh.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.solr.enabled=true
Whether to enable Solr health check.
How can I configure this property?
CAS Property: management.health.solr.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.solr.enabled=true
1
management:
health:
solr:
enabled: "true"
1
java -Dmanagement.health.solr.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_SOLR_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.solr.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
management.health.zookeeper.enabled=true
Enable the health endpoint for zookeeper.
How can I configure this property?
CAS Property: management.health.zookeeper.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
management.health.zookeeper.enabled=true
1
management:
health:
zookeeper:
enabled: "true"
1
java -Dmanagement.health.zookeeper.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export MANAGEMENT_HEALTH_ZOOKEEPER_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --management.health.zookeeper.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
spring.security.user.name=user
Default user name.
CAS Property:
|
1 | spring.security.user.name=user |
1
spring:
security:
user:
name: "user"
1
java -Dspring.security.user.name="user" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export SPRING_SECURITY_USER_NAME="user"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --spring.security.user.name="user"
cas.war
with an embedded server container and can be found in the build/libs directory.
spring.security.user.password=
Password for the default user name.
org.springframework.boot.autoconfigure.security.SecurityProperties$User.
CAS Property: spring.security.user.password
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
spring.security.user.password=...
1
spring:
security:
user:
password: "..."
1
java -Dspring.security.user.password="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export SPRING_SECURITY_USER_PASSWORD="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --spring.security.user.password="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
spring.security.user.roles=
Granted roles for the default user name.
org.springframework.boot.autoconfigure.security.SecurityProperties$User.
CAS Property: spring.security.user.roles
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
spring.security.user.roles=...
1
spring:
security:
user:
roles: "..."
1
java -Dspring.security.user.roles="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export SPRING_SECURITY_USER_ROLES="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --spring.security.user.roles="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
For basic authentication, the default username is casuser. The password may be automatically generated at startup and displayed in CAS logs if it is left undefined in CAS settings. Additional sources may also be defined that would authenticate the request via JAAS, LDAP, JDBC, etc.
Once endpoints are enabled and exposed, the security of all provided endpoints is handled by the Spring Security project. Protection and access to each endpoint is controlled via CAS settings individually such that you may decide a specific security level and method of authentication for each endpoint independently.
- If CAS is configured to NOT enforce endpoint security rules, then all endpoints are considered sensitive and require authentication, typically handled via basic authentication with master credentials defined in CAS settings.
- If CAS is configured to enforce endpoint security rules, then each endpoint may be tagged with a specific security rule allowing access via authorized IP addresses, basic credentials, roles and attributes, etc.
There is a special endpoint named defaults which serves as a shortcut that
controls the security of all endpoints, if left undefined in CAS settings.
To enable additional logging, configure the log4j configuration file to add the following levels:
1
2
3
4
5
6
7
8
<Logger name="org.pac4j" level="debug" additivity="false">
<AppenderRef ref="console" />
<AppenderRef ref="file" />
</Logger>
<Logger name="org.springframework.security" level="debug" additivity="false">
<AppenderRef ref="console" />
<AppenderRef ref="file" />
</Logger>
Configuration
JWT support is enabled by including the following dependency in the WAR overlay:
1
2
3
4
5
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-support-token-tickets</artifactId>
<version>${cas.version}</version>
</dependency>
1
implementation "org.apereo.cas:cas-server-support-token-tickets:${project.'cas.version'}"
1
2
3
4
5
6
7
8
9
dependencyManagement {
imports {
mavenBom "org.apereo.cas:cas-server-support-bom:${project.'cas.version'}"
}
}
dependencies {
implementation "org.apereo.cas:cas-server-support-token-tickets"
}
1
2
3
4
5
6
7
8
9
10
dependencies {
/*
The following platform references should be included automatically and are listed here for reference only.
implementation enforcedPlatform("org.apereo.cas:cas-server-support-bom:${project.'cas.version'}")
implementation platform(org.springframework.boot.gradle.plugin.SpringBootPlugin.BOM_COORDINATES)
*/
implementation "org.apereo.cas:cas-server-support-token-tickets"
}
The following settings and properties are available from the CAS configuration catalog:
- Required
- Optional
- Signing & Encryption
- Hibernate & JDBC
- Email Servers
- LDAP & Active Directory
- Authentication
- Password Encoding
- Principal Transformation
- Password Policy
- Notes
cas.authn.token.principal-transformation.groovy.location=
The location of the resource. Resources can be URLS, or files found either on the classpath or outside somewhere in the file system. In the event the configured resource is a Groovy script, specially if the script set to reload on changes, you may need to adjust the total number ofinotify instances. On Linux, you may need to add the following line to /etc/sysctl.conf: fs.inotify.max_user_instances = 256. You can check the current value via cat /proc/sys/fs/inotify/max_user_instances.
CAS Property:
|
1 | cas.authn.token.principal-transformation.groovy.location=... |
1
cas:
authn:
token:
principal-transformation:
groovy:
location: "..."
1
java -Dcas.authn.token.principal-transformation.groovy.location="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_PRINCIPAL_TRANSFORMATION_GROOVY_LOCATION="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.principal-transformation.groovy.location="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.encryption.key=
The encryption key is a JWT whose length is defined by the encryption key size setting.
org.apereo.cas.configuration.model.core.util.EncryptionJwtCryptoProperties.
CAS Property: cas.authn.token.crypto.encryption.key
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.encryption.key=...
1
cas:
authn:
token:
crypto:
encryption:
key: "..."
1
java -Dcas.authn.token.crypto.encryption.key="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ENCRYPTION_KEY="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.encryption.key="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.signing.key=
The signing key is a JWT whose length is defined by the signing key size setting.
org.apereo.cas.configuration.model.core.util.SigningJwtCryptoProperties.
CAS Property: cas.authn.token.crypto.signing.key
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.signing.key=...
1
cas:
authn:
token:
crypto:
signing:
key: "..."
1
java -Dcas.authn.token.crypto.signing.key="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_SIGNING_KEY="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.signing.key="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.principal-transformation.blocking-pattern=
A regular expression that will be used against the username to match for blocking/forbidden values. If a match is found, an exception will be thrown and principal transformation will fail.
CAS Property:
|
1 | cas.authn.token.principal-transformation.blocking-pattern=... |
1
cas:
authn:
token:
principal-transformation:
blocking-pattern: "..."
1
java -Dcas.authn.token.principal-transformation.blocking-pattern="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_PRINCIPAL_TRANSFORMATION_BLOCKING_PATTERN="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.principal-transformation.blocking-pattern="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.principal-transformation.case-conversion=NONE
Indicate whether the principal identifier should be transformed into upper-case, lower-case, etc. Available values are as follows:
NONE: No conversion.LOWERCASE: Lowercase conversion.UPPERCASE: Uppercase conversion.
org.apereo.cas.configuration.model.core.authentication.PrincipalTransformationProperties.
CAS Property: cas.authn.token.principal-transformation.case-conversion
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.principal-transformation.case-conversion=NONE
1
cas:
authn:
token:
principal-transformation:
case-conversion: "NONE"
1
java -Dcas.authn.token.principal-transformation.case-conversion="NONE" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_PRINCIPAL_TRANSFORMATION_CASE_CONVERSION="NONE"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.principal-transformation.case-conversion="NONE"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.principal-transformation.pattern=
A regular expression that will be used against the provided username for username extractions. On a successful match, the first matched group in the pattern will be used as the extracted username.
org.apereo.cas.configuration.model.core.authentication.PrincipalTransformationProperties.
CAS Property: cas.authn.token.principal-transformation.pattern
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.principal-transformation.pattern=...
1
cas:
authn:
token:
principal-transformation:
pattern: "..."
1
java -Dcas.authn.token.principal-transformation.pattern="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_PRINCIPAL_TRANSFORMATION_PATTERN="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.principal-transformation.pattern="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.principal-transformation.prefix=
Prefix to add to the principal id prior to authentication.
org.apereo.cas.configuration.model.core.authentication.PrincipalTransformationProperties.
CAS Property: cas.authn.token.principal-transformation.prefix
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.principal-transformation.prefix=...
1
cas:
authn:
token:
principal-transformation:
prefix: "..."
1
java -Dcas.authn.token.principal-transformation.prefix="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_PRINCIPAL_TRANSFORMATION_PREFIX="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.principal-transformation.prefix="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.principal-transformation.suffix=
Suffix to add to the principal id prior to authentication.
org.apereo.cas.configuration.model.core.authentication.PrincipalTransformationProperties.
CAS Property: cas.authn.token.principal-transformation.suffix
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.principal-transformation.suffix=...
1
cas:
authn:
token:
principal-transformation:
suffix: "..."
1
java -Dcas.authn.token.principal-transformation.suffix="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_PRINCIPAL_TRANSFORMATION_SUFFIX="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.principal-transformation.suffix="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.alg=
The signing/encryption algorithm to use.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.alg
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.alg=...
1
cas:
authn:
token:
crypto:
alg: "..."
1
java -Dcas.authn.token.crypto.alg="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ALG="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.alg="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.enabled=true
Whether crypto operations are enabled.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.enabled=true
1
cas:
authn:
token:
crypto:
enabled: "true"
1
java -Dcas.authn.token.crypto.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.encryption-enabled=true
Whether crypto encryption operations are enabled.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.encryption-enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.encryption-enabled=true
1
cas:
authn:
token:
crypto:
encryption-enabled: "true"
1
java -Dcas.authn.token.crypto.encryption-enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ENCRYPTION_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.encryption-enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.encryption.key-size=512
The encryption key size.
org.apereo.cas.configuration.model.core.util.EncryptionJwtCryptoProperties.
CAS Property: cas.authn.token.crypto.encryption.key-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.encryption.key-size=512
1
cas:
authn:
token:
crypto:
encryption:
key-size: "512"
1
java -Dcas.authn.token.crypto.encryption.key-size="512" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ENCRYPTION_KEY_SIZE="512"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.encryption.key-size="512"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.signing-enabled=true
Whether crypto signing operations are enabled.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.signing-enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.signing-enabled=true
1
cas:
authn:
token:
crypto:
signing-enabled: "true"
1
java -Dcas.authn.token.crypto.signing-enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_SIGNING_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.signing-enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.signing.key-size=512
The signing key size.
org.apereo.cas.configuration.model.core.util.SigningJwtCryptoProperties.
CAS Property: cas.authn.token.crypto.signing.key-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.signing.key-size=512
1
cas:
authn:
token:
crypto:
signing:
key-size: "512"
1
java -Dcas.authn.token.crypto.signing.key-size="512" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_SIGNING_KEY_SIZE="512"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.signing.key-size="512"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.strategy-type=ENCRYPT_AND_SIGN
Control the cipher sequence of operations. The accepted values are:
ENCRYPT_AND_SIGN: Encrypt the value first, and then sign.SIGN_AND_ENCRYPT: Sign the value first, and then encrypt.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.strategy-type
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.strategy-type=ENCRYPT_AND_SIGN
1
cas:
authn:
token:
crypto:
strategy-type: "ENCRYPT_AND_SIGN"
1
java -Dcas.authn.token.crypto.strategy-type="ENCRYPT_AND_SIGN" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_STRATEGY_TYPE="ENCRYPT_AND_SIGN"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.strategy-type="ENCRYPT_AND_SIGN"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.webflow.enabled=true
Whether webflow auto-configuration should be enabled.
org.apereo.cas.configuration.model.core.web.flow.WebflowAutoConfigurationProperties.
CAS Property: cas.authn.token.webflow.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.webflow.enabled=true
1
cas:
authn:
token:
webflow:
enabled: "true"
1
java -Dcas.authn.token.webflow.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_WEBFLOW_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.webflow.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.webflow.order=0
The order in which the webflow is configured.
org.apereo.cas.configuration.model.core.web.flow.WebflowAutoConfigurationProperties.
CAS Property: cas.authn.token.webflow.order
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.webflow.order=0
1
cas:
authn:
token:
webflow:
order: "0"
1
java -Dcas.authn.token.webflow.order="0" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_WEBFLOW_ORDER="0"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.webflow.order="0"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.name=
Name of the authentication handler.
org.apereo.cas.configuration.model.support.token.TokenAuthenticationProperties.
CAS Property: cas.authn.token.name
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.name=...
1
cas:
authn:
token:
name: "..."
1
java -Dcas.authn.token.name="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_NAME="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.name="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.state=
Define the scope and state of this authentication handler and the lifecycle in which it can be invoked or activated. Available values are as follows:
ACTIVE: Active authentication handler, and is invoked by default automatically to verify credentials globally.STANDBY: Authentication handler is in a semi-enabled state, waiting to be called only on-demand when explicitly asked for.
org.apereo.cas.configuration.model.support.token.TokenAuthenticationProperties.
CAS Property: cas.authn.token.state
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.state=...
1
cas:
authn:
token:
state: "..."
1
java -Dcas.authn.token.state="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_STATE="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.state="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.encryption.key=
The encryption key is a JWT whose length is defined by the encryption key size setting.
CAS Property:
|
1 | cas.authn.token.crypto.encryption.key=... |
1
cas:
authn:
token:
crypto:
encryption:
key: "..."
1
java -Dcas.authn.token.crypto.encryption.key="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ENCRYPTION_KEY="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.encryption.key="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.signing.key=
The signing key is a JWT whose length is defined by the signing key size setting.
org.apereo.cas.configuration.model.core.util.SigningJwtCryptoProperties.
CAS Property: cas.authn.token.crypto.signing.key
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.signing.key=...
1
cas:
authn:
token:
crypto:
signing:
key: "..."
1
java -Dcas.authn.token.crypto.signing.key="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_SIGNING_KEY="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.signing.key="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.alg=
The signing/encryption algorithm to use.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.alg
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.alg=...
1
cas:
authn:
token:
crypto:
alg: "..."
1
java -Dcas.authn.token.crypto.alg="..." -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ALG="..."
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.alg="..."
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.enabled=true
Whether crypto operations are enabled.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.enabled=true
1
cas:
authn:
token:
crypto:
enabled: "true"
1
java -Dcas.authn.token.crypto.enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.encryption-enabled=true
Whether crypto encryption operations are enabled.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.encryption-enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.encryption-enabled=true
1
cas:
authn:
token:
crypto:
encryption-enabled: "true"
1
java -Dcas.authn.token.crypto.encryption-enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ENCRYPTION_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.encryption-enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.encryption.key-size=512
The encryption key size.
org.apereo.cas.configuration.model.core.util.EncryptionJwtCryptoProperties.
CAS Property: cas.authn.token.crypto.encryption.key-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.encryption.key-size=512
1
cas:
authn:
token:
crypto:
encryption:
key-size: "512"
1
java -Dcas.authn.token.crypto.encryption.key-size="512" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_ENCRYPTION_KEY_SIZE="512"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.encryption.key-size="512"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.signing-enabled=true
Whether crypto signing operations are enabled.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.signing-enabled
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.signing-enabled=true
1
cas:
authn:
token:
crypto:
signing-enabled: "true"
1
java -Dcas.authn.token.crypto.signing-enabled="true" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_SIGNING_ENABLED="true"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.signing-enabled="true"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.signing.key-size=512
The signing key size.
org.apereo.cas.configuration.model.core.util.SigningJwtCryptoProperties.
CAS Property: cas.authn.token.crypto.signing.key-size
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.signing.key-size=512
1
cas:
authn:
token:
crypto:
signing:
key-size: "512"
1
java -Dcas.authn.token.crypto.signing.key-size="512" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_SIGNING_KEY_SIZE="512"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.signing.key-size="512"
cas.war
with an embedded server container and can be found in the build/libs directory.
cas.authn.token.crypto.strategy-type=ENCRYPT_AND_SIGN
Control the cipher sequence of operations. The accepted values are:
ENCRYPT_AND_SIGN: Encrypt the value first, and then sign.SIGN_AND_ENCRYPT: Sign the value first, and then encrypt.
org.apereo.cas.configuration.model.core.util.EncryptionOptionalSigningOptionalJwtCryptographyProperties.
CAS Property: cas.authn.token.crypto.strategy-type
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
.properties files:
1
cas.authn.token.crypto.strategy-type=ENCRYPT_AND_SIGN
1
cas:
authn:
token:
crypto:
strategy-type: "ENCRYPT_AND_SIGN"
1
java -Dcas.authn.token.crypto.strategy-type="ENCRYPT_AND_SIGN" -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory. Note the placement of the system property which must be
specified before the CAS web application is launched.
1
2
3
export CAS_AUTHN_TOKEN_CRYPTO_STRATEGY_TYPE="ENCRYPT_AND_SIGN"
java -jar build/libs/cas.war
cas.war
with an embedded server container and can be found in the build/libs directory.
1
java -jar build/libs/cas.war --cas.authn.token.crypto.strategy-type="ENCRYPT_AND_SIGN"
cas.war
with an embedded server container and can be found in the build/libs directory.
This CAS feature is able to accept signing and encryption crypto keys. In most scenarios if keys are not provided, CAS will auto-generate them. The following instructions apply if you wish to manually and beforehand create the signing and encryption keys.
Note that if you are asked to create a JWK of a certain size for the key, you are to use the following set of commands to generate the token:
1
2
wget https://raw.githubusercontent.com/apereo/cas/master/etc/jwk-gen.jar
java -jar jwk-gen.jar -t oct -s [size]
The outcome would be similar to:
1
2
3
4
5
{
"kty": "oct",
"kid": "...",
"k": "..."
}
The generated value for k needs to be assigned to the relevant CAS settings. Note that keys generated via
the above algorithm are processed by CAS using the Advanced Encryption Standard (AES) algorithm which is a
specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology.
RSA Keys
Certain CAS features such as the ability to produce JWTs as CAS tickets
may allow you to use the RSA algorithm with public/private keypairs for signing and encryption. This
behavior may prove useful generally in cases where the consumer of the CAS-encoded payload is an
outsider and a client application that need not have access to the signing secrets directly and
visibly and may only be given a half truth vis-a-vis a public key to verify the payload authenticity
and decode it. This particular option makes little sense in situations where CAS itself is both
a producer and a consumer of the payload.
Signing and encryption options are not
mutually exclusive. While it would be rather nonsensical, it is entirely possible for CAS to
use AES keys for signing and RSA keys for encryption, or vice versa.
In order to enable RSA functionality for signing payloads, you will need to generate a private/public keypair via the following sample commands:
1
2
openssl genrsa -out private.key 2048
openssl rsa -pubout -in private.key -out public.key -inform PEM -outform DER
The private key path (i.e. file:///path/to/private.key) needs to be configured for the
signing key in CAS properties for the relevant feature. The public key needs to be shared
with client applications and consumers of the payload in order to validate the payload signature.
Remember that RSA key sizes
are required to be at least 2048 and above. Smaller key sizes are not
accepted by CAS and will cause runtime errors. Choose wisely.
In order to enable RSA functionality for encrypting payloads, you will need to essentially
execute the reverse of the above operations. The client application will provide you with
a public key which will be used to encrypt the payload and whose path (i.e. file:///path/to/public.key)
needs to be configured for the encryption key in CAS properties for the relevant feature.
Once the payload is submitted, the client should use its own private key to decode the payload and unpack it.
Authentication handlers that generally deal with username-password credentials can be configured to transform the user id prior to executing the authentication sequence. Each authentication strategy in CAS provides settings to properly transform the principal. Refer to the relevant settings for the authentication strategy at hand to learn more.
Authentication handlers as part of principal transformation may also be provided a path to a Groovy script to transform the provided username. The outline of the script may take on the following form:
1
2
3
4
5
String run(final Object... args) {
def providedUsername = args[0]
def logger = args[1]
return providedUsername.concat("SomethingElse")
}
Configuration Metadata
The collection of configuration properties listed in this section are automatically generated from the CAS source and components that contain the actual field definitions, types, descriptions, modules, etc. This metadata may not always be 100% accurate, or could be lacking details and sufficient explanations.
Be Selective
This section is meant as a guide only. Do NOT copy/paste the entire collection of settings into your CAS configuration; rather pick only the properties that you need. Do NOT enable settings unless you are certain of their purpose and do NOT copy settings into your configuration only to keep them as reference. All these ideas lead to upgrade headaches, maintenance nightmares and premature aging.
YAGNI
Note that for nearly ALL use cases, declaring and configuring properties listed here is sufficient. You should NOT have to explicitly massage a CAS XML/Java/etc configuration file to design an authentication handler, create attribute release policies, etc. CAS at runtime will auto-configure all required changes for you. If you are unsure about the meaning of a given CAS setting, do NOT turn it on without hesitation. Review the codebase or better yet, ask questions to clarify the intended behavior.
Naming Convention
Property names can be specified in very relaxed terms. For instance cas.someProperty, cas.some-property, cas.some_property are all valid names. While all
forms are accepted by CAS, there are certain components (in CAS and other frameworks used) whose activation at runtime is conditional on a property value, where
this property is required to have been specified in CAS configuration using kebab case. This is both true for properties that are owned by CAS as well as those
that might be presented to the system via an external library or framework such as Spring Boot, etc.
When possible, properties should be stored in lower-case kebab format, such as cas.property-name=value.
The only possible exception to this rule is when naming actuator endpoints; The name of the
actuator endpoints (i.e. ssoSessions) MUST remain in camelCase mode.
Settings and properties that are controlled by the CAS platform directly always begin with the prefix cas. All other settings are controlled and provided
to CAS via other underlying frameworks and may have their own schemas and syntax. BE CAREFUL with
the distinction. Unrecognized properties are rejected by CAS and/or frameworks upon which CAS depends. This means if you somehow misspell a property definition
or fail to adhere to the dot-notation syntax and such, your setting is entirely refused by CAS and likely the feature it controls will never be activated in the
way you intend.
Validation
Configuration properties are automatically validated on CAS startup to report issues with configuration binding, specially if defined CAS settings cannot be
recognized or validated by the configuration schema. The validation process is on by default and can be skipped on startup using a special system
property SKIP_CONFIG_VALIDATION that should be set to true. Additional validation processes are also handled
via Configuration Metadata and property migrations applied automatically on
startup by Spring Boot and family.
Indexed Settings
CAS settings able to accept multiple values are typically documented with an index, such as cas.some.setting[0]=value. The index [0] is meant to be
incremented by the adopter to allow for distinct multiple configuration blocks.
Register Clients
Signal the relevant application in CAS service registry to produce JWTs for service tickets:
1
2
3
4
5
6
7
8
9
10
11
12
13
{
"@class" : "org.apereo.cas.services.CasRegisteredService",
"serviceId" : "^https://.*",
"name" : "Sample",
"id" : 10,
"properties" : {
"@class" : "java.util.HashMap",
"jwtAsServiceTicket" : {
"@class" : "org.apereo.cas.services.DefaultRegisteredServiceProperty",
"values" : [ "java.util.HashSet", [ "true" ] ]
}
}
}
Configure Keys Per Service
By default, the signing and encryption keys used to encode the JWT are global to the CAS server and can be defined via CAS settings. It is also possible to override the global keys on a per-service basis, allowing each application to use its own set of signing and encryption keys. To do so, configure the service definition in the registry to match the following:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
{
"@class" : "org.apereo.cas.services.CasRegisteredService",
"serviceId" : "^https://.*",
"name" : "Sample",
"id" : 10,
"properties" : {
"@class" : "java.util.HashMap",
"jwtAsServiceTicket" : {
"@class" : "org.apereo.cas.services.DefaultRegisteredServiceProperty",
"values" : [ "java.util.HashSet", [ "true" ] ]
},
"jwtAsServiceTicketSigningKey" : {
"@class" : "org.apereo.cas.services.DefaultRegisteredServiceProperty",
"values" : [ "java.util.HashSet", [ "..." ] ]
},
"jwtAsServiceTicketEncryptionKey" : {
"@class" : "org.apereo.cas.services.DefaultRegisteredServiceProperty",
"values" : [ "java.util.HashSet", [ "..." ] ]
},
"jwtAsServiceTicketCipherStrategyType" : {
"@class" : "org.apereo.cas.services.DefaultRegisteredServiceProperty",
"values" : [ "java.util.HashSet", [ "ENCRYPT_AND_SIGN" ] ]
}
}
}
The following cipher strategy types are available:
| Type | Description |
|---|---|
ENCRYPT_AND_SIGN |
Default strategy; encrypt values, and then sign. |
SIGN_AND_ENCRYPT |
Sign values, and then encrypt. |
The following properties are available and recognized by CAS for various modules and features:
| Name | Default Value | Type | Group |
|---|---|---|---|
jwtAsServiceTicket
|
false
|
BOOLEAN
|
JWT_SERVICE_TICKETS
|
jwtAsServiceTicketCipherStrategyType
|
ENCRYPT_AND_SIGN
|
STRING
|
JWT_SERVICE_TICKETS
|
jwtAsServiceTicketSigningKey
|
|
STRING
|
JWT_SERVICE_TICKETS
|
jwtAsServiceTicketEncryptionKey
|
|
STRING
|
JWT_SERVICE_TICKETS
|
JWT Validation - AES
The following example code snippet demonstrates how one might go about validating and parsing the CAS-produced JWT
that is created using shared secrets via AES:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
import org.apache.commons.codec.binary.Base64;
import org.jose4j.jwe.JsonWebEncryption;
import org.jose4j.jwk.JsonWebKey;
import org.jose4j.jws.JsonWebSignature;
import org.jose4j.keys.AesKey;
import java.nio.charset.StandardCharsets;
import java.security.Key;
...
var signingKey = "...";
var encryptionKey = "...";
var key = new AesKey(signingKey.getBytes(StandardCharsets.UTF_8));
var jws = new JsonWebSignature();
jws.setCompactSerialization(secureJwt);
jws.setKey(key);
if (!jws.verifySignature()) {
throw new Exception("JWT verification failed");
}
var decodedBytes = Base64.decodeBase64(jws.getEncodedPayload().getBytes(StandardCharsets.UTF_8));
var decodedPayload = new String(decodedBytes, StandardCharsets.UTF_8);
var jwe = new JsonWebEncryption();
var jsonWebKey = JsonWebKey.Factory
.newJwk("\n" + "{\"kty\":\"oct\",\n" + " \"k\":\"" + encryptionKey + "\"\n" + "}");
jwe.setCompactSerialization(decodedPayload);
jwe.setKey(new AesKey(jsonWebKey.getKey().getEncoded()));
System.out.println(jwe.getPlaintextString());