The contents of this blog are managed and hosted on Github. If you wish to update the contents of this post, please submit a pull request to this repository.
The official CAS 5.1.0 GA was released on May 27th 2017. Since then,
the project has been moving forward with development of the next feature release
that is tagged as 5.2.0. This post intends to highlight some of the improvements
and enhancements packed into the third release candidate in the 5.2.0 series.
The in-development documentation of CAS 5.2.0 is available here.
The release schedule is also available here. The release policy
is available here.
You can read more about the previous release candidate here.
- Shake Well Before Use
- Minors
- Management Web Application Redesign
- Authentication Events
- Caffein for Guava Caching
- SAML2 Service Provider Integrations
- Monitoring
- Authentication Interrupt
- JMeter Performance Testing
- Attribute Consent
- Time-based Multifactor Authentication Trigger
- Protocol Attributes Release per Service
- OAuth & OpenID Connect
- Unique Principal Authentication Policy
- MongoDb Configuration
- Surrogate Authentication
- FIDO U2F MFA
- Audit Storage
- Acceptable Usage Policy
- Memcached Ticket Registry
- Redis Service Registry
- SAML2 Improvements
- Library Upgrades
- Get Involved
- Das Ende
Shake Well Before Use
We strongly recommend that you take advantage of the release candidates as they come out. Waiting for a GA release is only going to set you up for unpleasant surprises. A GA is simply a tag and nothing more. In order to start experimenting with release candidates, use the following strategies.
At any given time, you should be able to append -SNAPSHOT to the CAS version specified in order to take advantage of snapshot builds as changes are made and published.
Apache Maven
In the pom.xml of the overlay, adjust the following tag to match below:
<cas.version>5.2.0-RC3</cas.version>
Gradle
In the gradle.properties of the overlay, adjust the following tag to match below:
cas.version=5.2.0-RC3
Minors
- MongoDb authentication is improved to honor the MongoDb connection pool and threads which monitor that pool.
- The default port for the management web application when run in embedded mode is now switched to
8444to avoid conflicts with the main CAS web application server when both are run in the same environment. - Thanks to @karlbanke, MongoDb functionality gains a few new additional settings that control ssl, replicas, etc.
- The default ability of defining Spring beans in XML inside the management web application has been removed.
- Thanks to @tsschmidt, the
/statusendpoint is now changed to run synchronous blocking mode to avoid side effects. - The default ability of defining Spring beans in XML/Groovy inside the CAS web application has been removed.
- The management web application is now able to advertise readiness in logs via ascii art.
- Thanks to @scalding, generating persistent ids in a Shibboleth-friendly way now correctly takes into account the salt and more.
- Thanks to @robertoschwald, generating primary keys for hibernate schemas is improved to take on a more
nativeapproach with some caveats documented that affect MySQL while running in a Galera cluster. - Thanks to @tduehr, generating random secure strings falls back to a more performant though ever-so-slightly less secure strategy and algorithm until Java 9 is released.
- The multifactor trusted device functionality for Google Authenticator and Swivel now correctly registers the relevant MFA flow into the CAS webflow engine at runtime.
- Thanks to @arbner, SAML MDUI functionality is now able to parse fields based on localized values correctly.
- Thanks to @arbner, consent functionality is now able to recognize the relevant service when used in SAML IdP mode.
- Thanks to @pdrados, the attribute name carrying the principal DN as part of LDAP authentication is now set to a static fixed name to avoid attribute encoding issues and easier release policies.
- A number of small readjustments to schemas that deal with storing trusted device records in databases, in cases where a number of field names clashes with reserved database keywords.
- Thanks to @SRieckhoff, a possible NPE with SPNEGO authentication is now prevented.
- SAML1 validation response is now updated in the documentation to ensure it matches the structure produced by CAS.
- Thanks to @tduehr, Apache Ignite support is given the ability to run in client mode.
- Thanks to @kingjared, generating SAML1 assertions gains an
issueLengthproperty to set the interval between theNotBeforeandNotOnOrAftertimestamps. - The JSON rendering performance of the CAS validation payload is significantly improved.
Management Web Application Redesign
Huge thanks to @tsschmidt, the CAS management web application is given an entirely new facelift and redesign using Material UI and Angular 4 based on Typescript. Aside from the fantastic new looks, the application is now able to support and handle most if not all of the configuration knobs and tweaks one can apply to a given service definition. This is a huge milestone allowing for a more solid foundation to start building much fancier integrations and features, such as auto-expiring services, approval workflows and more.
Here are a few sample screenshots:




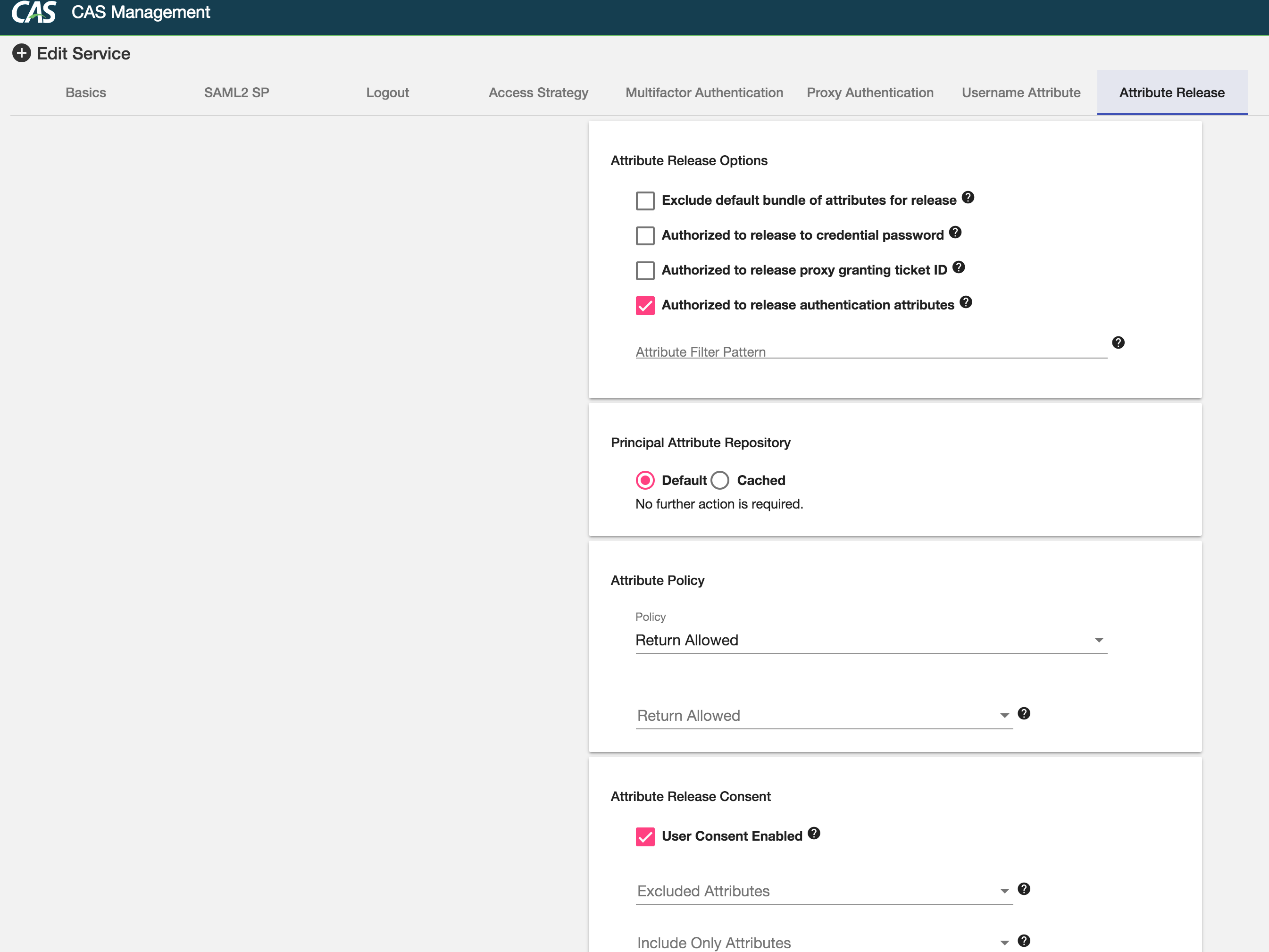

Authentication Events
InfluxDb Storage
CAS authentication events now gain the ability to use InfluxDb for storage.
Caffein for Guava Caching
Most if not all internal caching strategies and policies have switched from using the Guava library to Caffein. This is for the most part an invisible change, yet the swich allows CAS to dictate more granular expiration policies for caches that apply to each individual entry in the cache, rather than the cache itself as a whole.
SAML2 Service Provider Integrations
A number of new SAML2 service provider integrations are added to settings that include New Relic, Egnyte and more.
Monitoring
MongoDb
A new monitor is now included that is able to report back status and statistics on a MongoDb instance.
Ehcache
The Ehcache monitor is now improved to ensure it can work correctly with its ticket registry, taking into account caches created dynamically by the ticket catalog.
Memcached
The configuration of the memcached monitor is now moved into a separate block in order to leverage and provide support for connection pooling.
Authentication Interrupt
CAS has the ability to pause and interrupt the authentication flow to reach out to external services and resources, querying for status and setings that would then dictate how CAS should manage and control the SSO session. Interrupt services are able to present notification messages to the user, provide options for redirects to external services, etc. A common use case of this functionality deals with presenting a bulletin board during the authentication flow to present messages and announcements to select users and then optionally require that audience to complete a certain task before CAS is able to honor the authentication request and establish a session.
See this guide for more info.
JMeter Performance Testing
Thanks to @astohn, JMeter scripts for performance and stress testing CAS are now available.
Attribute Consent
LDAP Storage
Thanks to @arbner, attribute consent gains a new storage option to save decisions in LDAP. See this guide for more info.
Policy Per Service
Handling attribute consent now takes on a more wholesome API approach where there exists a consentPolicy that can dictate how attribute are selected and qualified for consent. See this guide for more info.
MongoDb Storage
A new storage option is now added to include support for MongoDb. See this guide for more info.
Schema Change
The structure of a consent decision is changed to rename the field date to createdDate, in to avoid collisions when the storage option is one of JDBC where date is considered a reserved keyword. You may need to readjust the schema manually in order to have CAS recognize existing records.
Time-based Multifactor Authentication Trigger
Adaptive authentication can also be configured to trigger multifactor authentication based on specific days and times.
See this guide for more info.
Protocol Attributes Release per Service
Attribute release policies gain a small setting to control whether the application is authorized and allowed to receive authentication/protocol attributes. See this guide for more info.
OAuth & OpenID Connect
Authorized Grant/Response Types
OAuth and OpenID Connect service definitions now get to specify the list of supported and authorized response and grant types. Note that for the time being, the absence of authorized response and grant types in the configration simply means the service is allowed to accept everything though this may change in the future.
Additionally, some foundational work is done to allow for parsing of requested scopes so they can later be mapped to attribute and claim release policies.
Token Revocation
Support for revoking OpenID Connect access/refresh tokens is now included in this release.
Pairwise Subject Identifiers
OpenID Connect support in CAS now presents the ability to support different subject types. This specifically includes support for pairwise subject id generation. See this guide for more info.
Unique Principal Authentication Policy
An additional authentication policy is now provided that can prevent an authentication event, if the user has already logged on and has a session with CAS.
MongoDb Configuration
In refactoring a number of configuration classes that deal with MongoDb settings, the MongoDb service registry is changed slightly to use a collection property rather than collectionName in order to keep things consistent across all settings. Similarly, a number of property placeholders have changed from mongodb to simply just mongo in order to again ensure a consistent naming strategy is used everywhere.
Surrogate Authentication
Surrogate authentication (Impersonation) gains the ability to dictate an expiration policy assigned to a surrogate session. Additionally, surrogate account storage and querying can now be done via a REST resource as well. Access strategies for impersonation are also improved to allow per-service authorization rules.
Note that the baseline module to include in the overlay has changed in this release candidate to clearly separate core and webflow functionality. Consult this guide for more info.
FIDO U2F MFA
MongoDb Storage
Device registration records for FIDO U2F may now be saved inside a MongoDb instance.
Audit Storage
Audit logs are now given the ability to store audit records inside a MongoDb database.
Acceptable Usage Policy
AUP support gains the ability store decisions via JDBC and REST. Note that the baseline module to include in the overlay has changed in this release candidate to clearly separate core and webflow functionality.
Memcached Ticket Registry
Performance
The registry has long carried the behavior to execute blocking ticket operations. In this release candidate, the registry switches to a more asynchronous model to gain maximum performance.
Connection Pooling
Memcached client instances are now pooled and during ticket registry operations are borrowed from and then returned to the pool in order to ensure maximum performance.
Redis Service Registry
A new service registry implementation based on Redis is now available.
SAML2 Improvements
The CAS project strives to conform to the SAML V2.0 Implementation Profile for Federation Interoperability. An evaluation of the requirements against the current CAS release is available here. It is RECOMMENDED that you view, evaluate and comment on functionality that is currently either absent or marked questionable where verification is needed.
SAML2 capabilities of CAS in this release provide support for the following:
- Metadata caching can be controlled via the
validUntilelement in the entity metadata. - A new attribute release filter is now available based on metadata entity attributes.
- A new attribute release filter is now available to release attributes based on requested attributes specified in the SP metadata.
- All signing operations are now able to consult metadata in order to resolve signing keys and iterate through all to find a successful matching candidate.
SAML2 Artifact Resolution
SAML2 capabilities of CAS in this release add support for the Artifact Resolution profile. See this guide for more info.
SAML2 Attribute Queries
SAML2 capabilities of CAS in this release add support for the Attribute Query profile. See this guide for more info.
SAML2 POST SimpleSign
SAML2 capabilities of CAS in this release add support for the POST SimpleSign profile. See this guide for more info.
Library Upgrades
- Spring Shell
- Spring Cloud Sleuth
- Apache Fediz
- Apache Fortress
- Spring Boot Admin
- Hibernate Validator
- MongoDb Driver
- Guava
- Caffein
- Amazon SDK
- Apache Tomcat
- Google Maps
- Twillio
- Kryo
- PostgreSQL
- MariaDb Driver
- Jose4J
- Apache Ignite
- Couchbase Driver
- Thymeleaf
- Infinispan
- Dropwizard Metrics
Get Involved
- Start your CAS deployment today. Try out features and share feedback.
- Better yet, contribute patches.
- Suggest and apply documentation improvements.
Das Ende
A big hearty thanks to all who participate in the development of this release to submit patches, report issues and suggest improvements. Keep’em coming!